CMMC Scope – Understanding the Sprawl

Table of contents
The CMMC program contains complex, and potentially confusing, scope requirements. Contractors that are preparing for a CMMC assessment will need to pay close attention to these requirements to achieve compliance. This includes contractors that currently meet the requirements of the DFARS 252.204-7012 contract clause due to changes in how the scope is defined. This post will explain the CMMC scope requirements and compare them to the requirements of the existing FAR 52.204-21 and DFARS 252.204-7012 requirements that CMMC is based on.
Information in this post is derived from the regulations that define the CMMC program at 32 CFR Part 170 and the scoping guides for the various CMMC Levels available on the Department of War CIO CMMC page. Unfortunately, these sources are occasionally self-contradictory and often leave room for interpretation so it shouldn’t be surprising to find some guidance that varies slightly from what is presented here.
TrustedSec is a CMMC Registered Practitioner Organization (RPO) that can help contractors understand how to determine and minimize their CMMC scope as well as assess compliance with the requirements that apply to the scope. Please get in touch with us if you need help building an efficient and effective compliance program.
Basic Scope
This section provides a high-level overview of what assets are considered in and out-of-scope for CMMC. There is nuance to how CMMC applies to these in-scope assets depending on the applicable CMMC level and the reason why the asset is in scope. The details of the scope definitions for each CMMC levels and asset categories are explored in more detail below.
The following flowchart can be used as a quick guide to determine whether assets are in or out-of-scope. A more detailed flowchart that contains the specific requirements for each level and asset category is provided later in this post.

Download Flowchart PDF
FCI and CUI
The scope of CMMC is based on the flow of two types of information, Federal Contract Information (FCI) and Controlled Unclassified Information (CUI), so it is important to understand what these are.
Contractors that are not handling FCI and/or CUI, or are handling these types of information on behalf of any government agency other than the Department of War, likely do not have CMMC compliance obligations and should review our previous post on Why You Don't Need to be CMMC Compliant.
FCI
FCI is any information provided by or generated for the government under a contract to develop or deliver a product or service to the government that is not intended for public release. There is an exception for simple transactional information, such as information necessary to process payments.
FCI does not carry any specific markings, and it is up to a contractor to understand whether information provided by or generated for the government under a contract is not intended for public release and is, therefore, FCI.
CUI
From a contractor’s perspective, CUI is either:
- Information the contractor receives from the government or upstream contractors that carries standardized CUI markings
- Information that a contractor creates that the contractor has been specifically instructed to apply CUI the markings to by the government or upstream contractors
For CMMC purposes, CUI can be considered a subset of FCI that requires extra protection.
CUI is narrowly defined and is not a catch-all designation for nearly all information sent to contractors (that’s what FCI is). CUI markings may only be applied when the government itself is required to safeguard or limit the dissemination of information due to specific laws, regulations, or government-wide policies. Contractors that are unsure of what information is CUI can review our previous post on Dealing With Unmarked and Mismarked CUI.
In-Scope Assets
At a high-level, the following assets (the CMMC term for system components or devices) are in scope for a contractor’s CMMC compliance program:
- Level 1 includes contractor assets that:
- Process, store, or transmit FCI
- Level 2 (and possibly Level 3) includes contractor and External Service Provider assets that:
- Process, store, or transmit CUI
- Can process, store, or transmit CUI even if they are not intended to
- Are not physically or logically separated from assets that process, store, or transmit CUI
- Provide security functions or capabilities for any assets that are in scope for Level 2 and/or 3 as per the points above
- Level 2 also includes External Service Provider assets that process, store, or transmit information relevant to the security of the contractor’s systems
The contractor’s CMMC scope will include their own assets as well as External Service Provider assets (potentially including cloud services) that meet the scope criteria above. This is explained in more detail below.
Out-of-Scope Assets
Endpoints that can only access FCI or CUI via a virtual desktop client are explicitly excluded from the CMMC scope if they are configured to not allow any processing, storage, or transmission of FCI and CUI beyond the Keyboard/Video/Mouse sent to the virtual desktop client.
Otherwise, to be considered out-of-scope for CMMC an asset must:
- Not process, store, or transmit FCI
- Not process, store, or transmit CUI
- Not be able to process, store, or transmit CUI
- Not provide security protections for assets that process, store, or transmit CUI
- Be physically or logically separated (i.e., network isolation) from assets that process, store, or transmit CUI.
Scope by Level
CMMC defines three levels, each of which has its own set of requirements and scope definition that determines how CMMC is applied. Each contract that contains the DFARS 252.204-7021 CMMC contract clause will indicate the highest level information handled under that individual contract will be subject to.
A single contractor may be simultaneously handling FCI and CUI subject to a combination of Level 1, Level 2, and Level 3 requirements under a single or multiple contracts and may have multiple systems certified at different CMMC Levels to handle this information. Contractors that are confused about what CMMC level they should expect can review our previous post on CMMC Level and Assessment Requirements for Defense Contractors.
Note that the Level 1 controls are a subset of the Level 2 controls, so any asset that falls into the Level 1 scope but operates using Level 2 controls can be considered compliant with Level 1 as well. Level 3 controls which only extend the Level 2 controls, so assets that fall within Level 3 will require the application of both Level 2 and Level 3 controls to be compliant.
Level 1
Level 1 is intended to protect FCI and uses the same 15 basic safeguards required by paragraph (b) of the existing FAR 52.204-21 contract clause for the protection of FCI. Defense contractors handling FCI should have already implemented the Level 1 controls as a result of their FAR 52.204-21 compliance program.
The Level 1 scope is formally defined in 32 CFR 170.19(b). The scope of both FAR 52.204-21 and Level 1 are also nearly identical: Under both FAR 52.204-21 and Level 1, the safeguards must be applied to any information system that is owned or operated by a contractor that processes, stores, or transmits FCI.
Level 1 makes two scope exceptions; the following are considered out-of-scope:
- Assets that can process, store, or transmit FCI but are unable to be fully secured (referred to as Specialized Assets)
- An endpoint hosting a virtual desktop client configured to not allow any processing, storage, or transmission of FCI beyond the Keyboard/Video/Mouse sent to the virtual desktop client
The definition of Specialized Assets is described in more detail below.
Contractors may want to be cautious about using these exceptions. Contractors that handle FCI are also likely subject to the FAR 52.204-21 clause for the safeguarding of FCI, which does not contain these same exceptions.
Level 2
Level 2 is intended to protect CUI and uses the same NIST SP 800-171r2 controls required by paragraph (b)(2)(i) the existing DFARS 252.204-7012 contract clause for the protection of CUI. Defense contractors handling CUI should already have implemented the Level 2 controls on any assets directly processing, storing, or transmitting CUI as a result of their DFARS 252.204-7012 compliance program.
The Level 2 scope is formally defined in 32 CFR 170.19(c). Level 2 requires the application of the NIST SP 800-171 controls across a much broader scope than what is required under DFARS 252.204-7012 and defines four categories of assets that are in scope:
- CUI Assets: Assets that process, store, or transmit CUI.
- Specialized Assets: Assets that can process, store, or transmit CUI but are unable to be fully secured.
- Contractor Risk Managed Assets: Assets that can, but are not intended to, process, store, or transmit CUI because of security policy, procedures, and practices in place.
- Security Protection Assets: Assets that provide security functions or capabilities to any of the other in scope assets listed above.
The Level 2 requirements apply to each of these asset categories in slightly different ways, and there is some nuance to the definitions of each asset category. This is all explained in detail below. Many contractors seem to be confused about the definitions of Specialized Assets and Contractor Risk Managed Assets in particular.
What CMMC refers to as CUI Assets should already have the NIST SP 800-171 controls implemented under the DFARS 252.204-7012 scope, but the other three asset categories are not within the DFARS 252.204-7012 scope and will need to be brought into compliance to achieve Level 2 certification. CMMC also applies the Level 2 controls to the assets of External Service Providers as explained below.
Level 2 also makes a scope exception, allowing endpoints hosting a virtual desktop client configured to not allow any processing, storage, or transmission of CUI beyond the Keyboard/Video/Mouse sent to the virtual desktop client to be treated as out-of-scope. This does not conflict with any requirements of DFARS 252.204-7012.
Level 3
Level 3 is also intended to protect CUI but introduces additional controls to “safeguard mission critical or unique technologies and programs”. Level 3 builds on the NIST SP 800-171 controls required by DFARS 252.204-7012 and Level 2 with additional controls from NIST SP 800-172. The NIST SP 800-172 controls were not previously required and will be new to contractors with Level 3 obligations.
The Level 3 scope is formally defined in 32 CFR 170.19(d). The scope of Level 3 is identical to Level 2, as described above, with one exception: Assets that would fall into the definition of a Contractor Risk Managed Assets category under Level 2 are considered CUI Assets under Level 3.
Level 3 contains the same scope exception for virtual desktop clients as level 2.
External Service Providers
Outsourcing to External Service Providers (a CMMC term for third parties that support the contractor’s IT and/or cybersecurity operations with external people, technology, or facilities) is not a way to avoid CMMC compliance requirements.
It may come as a surprise to many contractors that a contractor subject to Level 2 or 3 cannot be CMMC compliant until all of the in-scope External Service Providers can also demonstrate CMMC compliance. It may also come as a surprise that contractor assets that connect to External Service Provider assets handling CUI, including cloud services, are in-scope for CMMC.
An External Service Provider is considered within the contractor’s scope if the External Service Provider handles a contractor’s CUI or Security Protection Data (SPD) on the External Service Provider’s systems. Contractors that fall in scope in this way will only have Level 2 compliance obligations, even if the contractor is subject to Level 3 requirements.
SPD is information relevant to the security of the contractor’s systems that are in scope for Level 2 and/or 3. Examples of SPD include any of the following related to in scope assets:
- Configuration data
- Audit logs
- Vulnerabilities
- Passwords
External Service Providers follow the same scope rules as contractors: follow the flow of CUI to identify CUI Assets and then identify Specialized Assets, Risk Managed Assets, and Security Protection Assets based on their relationship with CUI Assets.
Contractor assets that interact with External Service Provider assets also follow the same scope rules as any other asset, i.e., a contractor asset that connects to an External Service Provider asset that processes CUI, including a cloud service, is considered in scope no different than if it were to connect to the contractor’s own on-premises CUI Asset.
TrustedSec’s previous blog post on CMMC Subcontractors and Service Providers offers a deeper dive into the topic of External Service Providers under CMMC.
Asset Categories
The CMMC controls apply in subtly different ways depending on the asset category and the applicable CMMC level. This section describes the nuances of each asset category.
Regardless of CMMC level and asset category, all assets in scope for Level 2 or 3 must be documented in the:
- System Security Plan
- Asset Inventory
- Network Diagram
The following flowchart may be a useful tool to help understand the asset categories and control applicability:
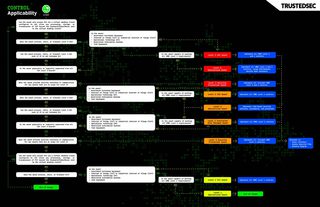
Download Flowchart PDF
FCI Assets
Control Applicability
FCI Assets must have all Level 1 controls applied.
Level 1 controls are a subset of Level 2 controls, so any asset that is brought into compliance with Level 2 or higher will also be compliant with Level 1.
Scope Definition
FCI Assets are assets that process, store, or transmit FCI.
The CMMC definitions of process, store, and transmit are covered in more detail for CUI Assets below but are almost irrelevant for FCI because most contractors apply Level 1 across the entire environment rather to only the systems that are technically in scope.
CUI Assets
Control Applicability
All CUI Assets must have Level 2 controls applied to them.
Level 3 CUI Assets must also have Level 3 controls applied to them in addition to the Level 2 controls.
Scope Definition
At Level 2, CUI Assets are assets that process, store, or transmit CUI.
Similarly, Level 3 CUI Assets are assets that can process, store, or transmit Level 3 CUI. Level 3 CUI Assets also include assets that meet the definition of a Contractor Risk Managed Asset (below) with regards to their relationship Level 3 CUI and Level 3 CUI Assets.
Process, Store, and Transmit
CMMC defines the terms process, store, and transmit as follows:
- Process: Data can be used by an asset (e.g., accessed, entered, edited, generated, manipulated, or printed)
- Store: Data is inactive or at rest on an asset (e.g., located on electronic media, in system component memory, or in physical format such as paper documents)
- Transmit: Data is being transferred from one asset to another asset (e.g., data in transit using physical or digital transport methods)
Contractors often seem to incorrectly exclude assets that:
- Do not store CUI, even if they process or transmit CUI
- Store CUI for very short periods of time
- Process, store, or transmit small amounts of CUI
- Process, store, or transmit CUI infrequently
Any processing, storage, or transmission of CUI puts an asset in scope for CMMC regardless of how infrequently or briefly it occurs and regardless of how few records are involved.
Workstations that process CUI are often overlooked because contractors mistakenly don’t consider any of the following to be processing:
- Loading CUI into applications and/or cloud services
- Editing CUI stored within applications and/or cloud services
- Retrieving CUI temporarily for transmission to another system or printing
Contractors also often overlook network infrastructure that transmits CUI, e.g., routers, switches, and Wi-Fi access points that CUI passes through. These are all potential CUI Assets.
Contractor Risk Managed Assets
Control Applicability
The concept of a Contractor Risk Managed Asset does not exist within Level 1 and any assets that meet this definition with regards to FCI can be considered out-of-scope for Level 1.
Level 2 Contractor Risk Managed Assets must have all Level 2 controls applied to them.
Any asset that would meet the definition of a Contractor Risk Managed Asset due to its interaction with Level 3 CUI or Level 3 CUI Assets is considered a Level 3 CUI Asset itself, rather than a Contractor Risk Managed Asset. These assets must have Level 2 and Level 3 controls applied in accordance with the requirements for CUI Assets.
Scope Definition
The definition of Contractor Risk Managed Assets is not as straightforward as CUI Assets and often confuses contractors. At the risk of oversimplifying, any asset that can establish a network connection to a CUI Asset should be considered a Contractor Risk Managed Asset unless proven otherwise.
This simplified definition is based on contrasting the formal CMMC definitions for Contractor Risk Managed Assets and Out-of-Scope Assets:
- Contractor Risk Managed Assets:
- “Assets that can, but are not intended to, process, store, or transmit CUI because of security policy, procedures, and practices in place”
- “Assets are not required to be physically or logically separated from CUI assets”
- Out-of-Scope Assets
- “Assets that cannot process, store, or transmit CUI; and do not provide security protections for CUI Assets”
- “Assets that are physically or logically separated from CUI Assets”
The first point of each definition tells us that assets that can process, store, or transmit CUI are Contractor Risk Managed and cannot be considered out-of-scope and must instead be considered a Contractor Risk Managed Asset. This concept of “can, but not intended to” is explored more below.
The second point of each definition tells us that assets must be physically or logically separated from CUI Assets to be considered out-of-scope, therefore those that are not separated must be Contractor Risk Managed Assets if they do not fall into the definitions any of the other asset categories. The concepts of physical and logical separation are also explored more below.
Again, keep in mind, Contractor Risk Managed Assets do not exist in CMMC Level 3. Any asset that meets this definition due to interaction with Level 3 CUI Assets is considered a CUI Asset instead.
Can, But Not Intended To…
It’s worth exploring what CMMC means by “can, but are not intended to process, store, or transmit CUI because of security policies, procedures, and practices in place”. Contractors will often try to claim an asset is out-of-scope even though it connects to a CUI Asset for a few reasons:
- There is a policy prohibiting the asset from accessing CUI
- There are procedures to prevent the asset from accidentally receiving CUI
- There are security practices (e.g., application, file, or folder permissions) that prohibit the asset from accessing CUI
All of these examples fall within the “security policies, procedures, and practices” that establish that the asset is “not intended to process, store, or transmit” CUI, which is what makes it a Contractor Risk Managed Asset rather than a CUI Asset. An asset can only be considered out-of-scope for CMMC if it absolutely cannot process, store, or transmit CUI. This is a high threshold. Often the easiest way to demonstrate that an asset cannot process, store, or transmit CUI is through physical or logical separation as described below.
Physically or Logically Separated…
It is also worth exploring what CMMC means by “physically or logically separated from CUI Assets”. The CMMC Level 2 Scoping Guide defines these as follows:
- Physical separation occurs when assets have no connection (wired or wireless). Data can only be transferred manually (e.g., USB drive).
- Logical separation occurs when data transfer between physically connected assets (wired or wireless) is prevented by non-physical means such as software or network assets (e.g., firewall, routers, VPNs, VLANs).
Physical separation is straightforward: An air gapped asset with no possible connection to a CUI Asset would be out-of-scope for CMMC unless it somehow meets the definition of another asset category besides Contractor Risk Managed Asset.
The definition of Logical Separation makes clear that data transfer must be prohibited to or from a physically connected CUI asset for an asset to be considered out-of-scope rather than a Contractor Risk Managed Asset. Prohibiting data transfer in such a manner is most often accomplished using a firewall that blocks all traffic between the asset intended to be out-of-scope and CUI Assets, although this can also be accomplished with newer zero-trust technologies that control network traffic on a host-by-host basis rather than with traditional firewalls. The mere presence of a firewall between two assets is not enough to implement logical separation, the out-of-scope assets must be completely isolated from the CUI assets by blocking rules.
Specialized Assets
Control Applicability
Specialized Assets are explicitly out-of-scope within Level 1 and any assets that meet this definition with regards to FCI can be considered out-of-scope for Level 1.
Level 2 Specialized Assets require risk-based security policies, procedure, and practices defined and implemented by the contractor. Ideally, the contractor should implement as many of the Level 2 controls as possible and use the risk-based approach to address the controls that cannot be implemented. An assessor may dig deeper if they have concerns about the risk-based program, so contractors should be prepared to show a risk assessment or other documentation to demonstrate how the security program is based on and sufficiently addresses risk.
Level 3 Specialized Assets must have all Level 2 and Level 3 controls applied to them, the risk-based approach used for Level 2 Specialized Assets is not allowed. Intermediary devices can be used to implement the controls that cannot be implemented on the Specialized Assets themselves, e.g., routing all access through a virtual desktop environment that implements the controls that cannot be implemented on the Specialized Asset itself.
Scope Definition
The CMMC regulations contain two separate definitions for Specialized Assets that differ from each other, but also have significant overlap, one in the Definitions section and the other in the Scope section. It seems that the intent of the combined definitions is that only the following asset types can be considered Specialized Assets, and even then, only if they cannot meet all of the applicable requirements for the appropriate CMMC level:
- Government Furnished Equipment
- Internet of Things (IoT) or Industrial Internet of Things (IIoT)
- Operational Technology (OT)
- Restricted Information Systems
- Test Equipment
Each of these specialized asset types is further defined in the CMMC Regulations or other regulations referenced by CMMC, as linked above.
Contractors should keep in mind that the Specialized Asset category is not a loophole that can be used to avoid implementing the requirements simply because the contractor is unwilling to do so. There must be some limitation that renders the asset unable to meet the requirements.
For example, consider the console on a CNC machine that manufactures parts using CUI data but does not support the authentication of individual users:
- The console should be in scope as a CUI asset because it stores and processes CUI.
- Control IA.L2-3.5.2 requires individuals to be authenticated before they access CUI.
- If the console does not support authentication of individuals, it cannot meet this requirement and therefore cannot be fully secured.
- The inability of the console to be fully secured renders it a Specialized Asset.
This scenario plays out similarly if the console uses only FCI rather than CUI except the applicable control would be IA.L1-B.1.VI (the Level 1 equivalent to IA.L2-3.5.2).
Security Protection Assets
Control Applicability
The concept of a Security Protection Asset does not exist within Level 1 and any assets that meet this definition with regards to FCI can be considered out-of-scope for Level 1.
Security Protection Assets must have all relevant Level 2 controls applied to them.
Level 3 Security Protection Assets must also have all relevant Level 3 control applied to them in addition to the relevant Level 2 controls. The concept of relevant controls is explained below.
Scope Definition
The formal definition of Security Protection Assets is that they provide security functions or capabilities to the contractor’s Level 2 and/or Level 3 Assessment Scope. The Level 2 and 3 Assessment Scope includes CUI Assets, Contractor Risk Managed Assets, and Specialized Assets as well as other Security Protection Assets.
Essentially, any asset that is used to implement a CMMC control for another in scope asset must be considered a Security Protection Asset. Examples include:
- Firewalls
- Assets that provide authentication services (e.g. domain controllers)
- Assets that provide log aggregation and alerting services (e.g., SIEMs)
- Configuration management tools
- Vulnerability scanning tools
- PKI infrastructure
- Endpoint security dashboards
- Etc.
Relevant Controls
What is meant by “relevant controls” is that:
- Many CMMC controls only make sense in the context of an asset that directly processes, stores, or transmit CUI and would not be relevant to Security Protection Assets.
- Other controls would be implemented by certain Security Protection Assets rather than broadly across the other assets in scope and are relevant only in the context of those Security Protection Assets
For example, consider a SIEM that collects and analyzes logs from CUI Assets:
- A SIEM typically would not process, store, or transmit CUI so control SC.L2-3.13.11, which requires the use of FIPS-validated cryptography to protect CUI, would not be relevant to the SIEM due to the lack of CUI to protect.
- Controls AU.L2-3.3.5 for audit log correlation and AU.L2-3.3.6 for audit record reduction and report generation are most likely to be implemented by a SIEM and therefore would be highly relevant on the SIEM.
- Other basic security controls, e.g., controls related to authentication, anti-malware, and vulnerability management are also just as relevant to the SIEM as they are to any other asset and are required.
Out-of-Scope Assets
Control Applicability
None of the CMMC controls apply to Out-of-Scope Assets at any level.
Scope Definition
To be considered out-of-scope, an asset must meet all of the following criteria:
- Cannot process, store, or transmit FCI
- Cannot process, store, or transmit CUI
- Does not provide security protections for CUI assets
- Is physically or logically separated from CUI assets
- Does not fall into the definition of any in-scope asset category
Also, keep the following scope exceptions in mind:
- Level 1 Specialized Assets are explicitly out-of-scope.
- The concepts of Contractor Risk Managed Assets and Security Protection Assets do not exist in Level 1 and are considered out-of-scope.
- Assets accessing FCI and/or CUI via a virtual desktop client that prohibits the transfer of FCI and CUI to the client is considered an Out-of-Scope Asset at all CMMC levels.
Cross-checking assets believed to be out-of-scope against this definition is a good exercise to identify assets that may have been missed when determining whether assets fall into the in-scope asset categories. If an asset does not meet the definition of an Out-of-Scope Asset, then it must fall into one of the in-scope asset categories (usually Contractor Risk Managed Assets).
Scope Minimization
The scope requirements described above can result in enormous scope creep, increasing the cost of compliance and disruption to business processes by dragging many of the organization’s systems into scope for CMMC. Alternatively, a strong understanding of the scope requirements can be leveraged to limit the scope of CMMC to the bare minimum number of assets.
The next post in this series will explore how the managing the flow of CUI and the structure of the network can be used to minimize the CMMC scope and reduce the overall cost of achieving and maintaining compliance.