CMMC NOPE: Why You Don’t Need to be CMMC Compliant

As a Cybersecurity Maturity Model Certification Registered Practitioner Organization (CMMC-RPO), TrustedSec fields many requests from organizations looking for help getting ready for the upcoming CMMC compliance requirements. Something that isn’t often talked about is how many government contractors and subcontractors will not need to be compliant, or may require compliance at a lower level than they were expecting.
September 30, 2025 update: This post has been updated to reflect the final version of CMMC and its contracting procedures.
CMMC Applicability
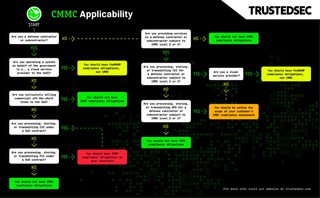
CMMC directly applies to organizations that are contractors or subcontractors of the U.S. Department of Defense (DoD) (32 CFR 170.3(c)) and also applies indirectly to defense contractors’ and subcontractors’ cloud and non-cloud external service providers. CMMC does not apply to organizations that are not doing any work for the DoD supply chain unless they plan to become a defense contractor or subcontractor (or provide services to defense contractors or subcontractors) in the future.
CMMC does not apply to defense contractors and subcontractors exclusively supplying commercially available off-the-shelf (COTS) items (32 CFR 170.3(c)). COTS includes commercial products sold in substantial quantities in the commercial marketplace and offered to the government, under a contract or subcontract, without modification, in the same form in which they are sold in the commercial marketplace (48 CFR 2.101).
CMMC only applies directly to defense contractors and subcontractors that handle two (2) specific types of information (32 CFR 170.3(a)) that have been subject to existing compliance requirements for nearly a decade:
- Federal Contract Information (FCI)
- Controlled Unclassified Information (CUI)
Additionally, CMMC may indirectly apply to your organization if you are providing services to a defense contractor or subcontractor and handle CUI or Security Protection Data (SPD) on their behalf.
CMMC will not apply to your organization if it is not storing, processing, and/or transmitting FCI, CUI, or SPD. The definitions of and methods for findings FCI, CUI, and SPD are covered later in this post.
Non-cloud external service providers that handle CUI on behalf of a contractor or subcontractor subject to CMMC Level 2 or 3 are in scope for their customers’ CMMC assessments (32 CFR 170.19(c)(2)(i)). External service providers (including cloud service providers) that handle the SPD of customers subject to CMMC will also have CMMC compliance obligations, even if they do not handle CUI (32 CFR 170.19(c)(2)(i)). When an external service provider handles CUI or SPD, their customers cannot be CMMC compliant unless the external service provider implements the applicable CMMC requirements on their systems that handle CUI and/or SPD and either voluntarily undergoes their own CMMC assessment or allows their customer to assess the external service providers’ compliance with CMMC.
Cloud providers that handle CUI on behalf of contractors and subcontractors subject to CMMC Level 2 or 3 requirements are considered external service providers but must implement FedRAMP Moderate baseline requirements rather than the CMMC requirements (32 CFR 170.19(c)(2)(i)). Cloud providers must provide their CMMC customers with FedRAMP authorization at the appropriate baseline or extensive information about their FedRAMP compliance program if they do not have a FedRAMP authorization.
CMMC does not apply to contractors or subcontractors that operate federal information systems on behalf of the government (32 CFR 170.3(b)). These systems are already subject to separate FedRAMP compliance requirements.
Implementing CMMC as a New Contractor Handling FCI or CUI
Some organizations that are not currently defense contractors or are defense contractors but are not currently handling FCI or CUI, may want to be prepared to bid on future DoD contracts with CMMC requirements. DoD will begin issuing solicitations and contracts with CMMC clauses as part of the CMMC phased rollout on November 10, 2025. Each solicitation and contract will define which CMMC Level is required and whether the contractor will be subject to a third-party assessment or may self-assess. Any organization may bid on these solicitations, but a contract cannot be awarded unless the bidder can demonstrate CMMC compliance at the appropriate level with the appropriate assessment type.
Because the CMMC requirements only apply to FCI and CUI, there is a sort of chicken-or-the-egg problem for contractors looking to break into this space. An organization cannot be awarded a contract until it has demonstrated it has implemented the requirements, but how can an organization demonstrate it can protect the information if it does not yet have any information to protect? In this scenario, TrustedSec recommends thinking through what types of FCI and CUI can reasonably be expected in future contracts and how the organization’s business processes will need to handle said FCI and CUI. A CMMC-ready environment can be built around these expectations so that it can be quickly adjusted and assessed once the final requirements are revealed during the bidding process.
What Are FCI, CUI, and SPD?
Most of the inquiries TrustedSec receives are from organizations that are in the DoD supply chain who worry that they will lose government contracts once CMMC is rolled out. Many of these organizations can’t articulate what FCI and CUI (and SPD in the case of external service providers) they are currently handling or expect to handle under future contracts. Understanding FCI, CUI, and SPD is essential for a defense contractor to know if they will have CMMC compliance obligations.
FCI and CUI have both existed and been subject to security requirements since 2016. Any organization that will be subject to CMMC when it is rolled out should already be aware that they are handling FCI and CUI and should be complying with the existing requirements for each of these information types.
FCI Defined
FCI is defined in FAR 4.1901 as “… information, not intended for public release, that is provided by or generated for the Government under a contract to develop or deliver a product or service to the Government, but not including information provided by the Government to the public (such as that on public Web sites) or simple transactional information, such as that necessary to process payments.”
This effectively covers nearly all non-public information handled under government contracts. Keep in mind, this definition does not cover proprietary information created independently of government contracts.
US Government contracts that involve handling FCI have and will continue to include the specific (and lengthy) contract clause, FAR 52.204-21. This clause does three (3) things:
- Defines FCI and the other terms used in the clause.
- Lists 15 basic security safeguards the contractor must implement to protect the systems that handle FCI.
- Requires the entire contract clause to be included in any subcontracts that involve the handling of FCI.
The 15 basic safeguards are relatively simple security requirements that every organization should have implemented as part of basic security best practices.
The new DFARS 252.204-7021 clause will add CMMC Level 1 requirements to the existing FAR 52.204-21 clause requirements in future defense contracts that involve handling FCI. CMMC Level 1 requires contractors to use the same 15 Basic Safeguards as FAR 52.204-21 but also requires a self-assessment.
CUI Defined
CUI is defined in 32 CFR 2002.4(h) as “…information the Government creates or possesses, or that an entity creates or possesses for or on behalf of the Government, that a law, regulation, or Government-wide policy requires or permits an agency to handle using safeguarding or dissemination controls. However, CUI does not include classified information or information a non-executive branch entity possesses and maintains in its own systems that did not come from, or was not created or possessed by or for, an executive branch agency or an entity acting for an agency…”
Many organizations are confused by this definition and think that much of the information they handle may be CUI as a result. There is a simpler way to understand CUI. CUI is unclassified information the government itself must protect because of specific laws, regulations, and policies that apply to narrowly defined types of information. Contractors become contractually obligated to protect that information when it is handled or created on behalf of the government.
Any CUI that the government sends to a contractor must have very specific markings that make it easy to identify. The government will also provide specific marking instructions if a contractor is expected to create CUI. Organizations that do not handle documents with CUI markings and have not received instructions to mark specific information as CUI are likely not receiving or generating CUI.
As with FCI, contracts that involve handling CUI have and will continue to include a specific contract clause. Some agencies have issued their own clauses and work is underway on a broad clause that will apply across all federal contracts but, as CMMC only applies to DoD contracts, we will focus exclusively on the DoD version of the clause. This clause is known as DFARS 252.204-7012 and does five things:
- Defines the various terms used in the clause.
- Requires cloud providers to implement the cloud security controls in DFARS 252.239-7010.
- Requires non-cloud contractors to implement the security requirements in National Institute of Standards and Technology Special Publication 800-171 (NIST SP 800-171) and use cloud services that meet FedRAMP Moderate requirements.
- Requires reporting of cyber incidents and establishes requirements for forensic analysis.
- Requires the entire contract clause be included in any subcontracts that involve the handling of CUI.
The security controls in NIST SP 800-171 that defense contractors and subcontractors handling CUI are already being required to implement under DFARS 252.204-7012 are a much more extensive set of controls than the 15 basic safeguards for FCI and are based on specific controls adapted from NIST SP 800-53.
Organizations that are subject to DFARS 252.204-7012 requirements for CUI will also be subject to a few more associated contract clauses:
- DFARS 252.204-7019 requires contractors perform NIST SP 800-171 self-assessments.
- DFARS 252.204-7020 allows the DoD to perform their own NIST SP 800-171 security assessments on certain contractors.
- DFARS 252.204-7024 requires contractors to report their NIST SP 800-171 self-assessment results to the DoD via the Supplier Performance Risk System (SPRS).
The new DFARS 252.204-7021 clause will add CMMC Level 2 or 3 requirements to these existing clauses in future defense contracts that involve handling of CUI. CMMC Level 2 requires contractors to use the same NIST SP 800-171 security controls for their own systems and FedRAMP Moderate requirements for cloud services as the DFARS 252.204.7012 clause but applies these requirements to a broader scope and in nearly all cases will require third-party audits where the existing clauses allowed self-assessments. CMMC Level 3 adds the NIST SP 800-172 security controls and will require audits by the DoD itself.
SPD Defined
SPD is a new CMMC specific term and only applies in the context of external service providers (including cloud service providers) working with defense contractors and subcontractors that are subject to CMMC Level 2 or 3 compliance.
SPD is defined in 32 CFR 170.4(b) as data used to protect the contractor’s systems that are subject to CMMC Level 2 or 3 requirements. SPD includes but is not limited to: Configuration data, log files, data related to configuration or vulnerability status, and passwords for the systems in scope for CMMC Level 2 or 3.
External service providers that handle SPD are within the scope of their customers’ CMMC assessments (32 CFR 170.19(c)(2)(i)).
Nonsense Contract Clauses
It is worth noting that there are many “fake” NIST SP 800-171 and CMMC contract clauses that do not use the official government text or define which CMMC levels and assessment types are required. See our post on fake CMMC contract clauses for more information on this topic.
TrustedSec advises against signing contracts with nonsense clauses and instead working with the other party to have the clauses removed from the contract if there is no FCI or CUI, or have the clauses updated to the text of the appropriate legitimate FAR and DFARS clauses if FCI and/or CUI will be handled.
Where is the FCI and CUI?
If your organization already has a robust compliance program for handling FCI and CUI in accordance with the 15 basic safeguards currently required by FAR 52.204-21 and the NIST SP 800-171 safeguarding controls currently required by DFARS 252.204-7012, then you will likely have a good handle on the presence and location of this information within your environment. Other organizations that are just realizing that they have been blissfully unaware of the handling requirements for the FCI and/or CUI they may already handle or are still unsure if they are handling FCI or CUI may need help determining where this information is.
The first step is to review existing contracts for the FAR 52.204-21, DFARS 252.204-7012, and/or (if you’re reading this after the CMMC rollout has begun) DFARS 252.204-7021 clauses. If none of the current contracts have these clauses, then it is unlikely the organization will be subject to CMMC compliance, at least without taking on new types of contracts.
The definition of FCI is very broad, so contractors that have a FAR 52.204-21 clause in their contracts should consider all information provided by or generated for the government under those contracts to be FCI unless the information is clearly intended for public release or is transactional information. Paperwork associated with solicitations and contracts that have DFARS 252.204-7012 or 252.204-7021 clauses should describe the CUI that will be handled under the contract (You may need to request these documents during the bidding process). When in doubt, ask the government contracting officer that issued the contract or subcontract what categories of CUI are expected under the contract.
An organization that believes CUI is in their environment but is unsure of where it is can also search the environment for CUI. The DoD publishes a CUI Marking training aid that provides a good overview of the markings the organization can search for. Documents containing CUI should already have these markings when they are received from third-parties, including the government and other contractors, and contractors that are creating CUI must include these markings on new documents that contain CUI as per DoD instructions.
Keep in mind, many contractors do not understand the CUI program and may apply incorrect markings to documents. See our post, Dealing With Unmarked and Mismarked CUI, for more information on how to identify CUI and what to do about suspicious markings.
Moving Up to CMMC
If you’ve found contracts with legitimate FAR 52.204-21, DFARS 252.204-7012, and/or DFARS 252.204-7021 clauses and have FCI and/or CUI in your environment, then you will need to implement CMMC to be awarded future defense contracts. Additionally, external service providers that handle CUI and/or SPD for their customers will also need to implement applicable CMMC (or FedRAMP, for cloud providers handling CUI) requirements.
The CMMC requirements are divided into three (3) levels, each of which is based on another set of security requirements that already exists:
- CMMC Level 1 covers FCI and consists of the 15 basic safeguards from FAR 52.204-21.
- CMMC Level 2 covers CUI and consists of the security controls in NIST SP 800-171
- CMMC Level 3 covers specific types of CUI (indicated in contracts) and consists of the security requirements in NIST SP 800-172.
CMMC contracts will indicate the required level and assessment type, but organizations that are preparing for CMMC will need to know what to expect. Our post on CMMC Level and Assessment Requirements for Defense Contractors can help understand and prepare for the appropriate requirements.
Organizations that will fall in scope for CMMC but have not implemented the applicable 15 safeguards from FAR 52.204-21 or the NIST SP 800-171 controls from DFARS 252.204-7012 should immediately begin implementing those programs both as a steppingstone to CMMC and because they have been required for years, likely putting an organization that has not implemented them in breach of their current contracts.
Because the CMMC requirements overlap with the FAR 52.204-21 and DFARS 252.204-7012 clauses, organizations that are already safeguarding FCI and CUI in accordance with these requirements should have little difficulty transitioning to CMMC except for two (2) significant changes:
- The scope of NIST SP 800-171 controls within CMMC Level 2 is broader than it is under DFARS 252.204-7012.
- The NIST SP 800-172 controls required by CMMC Level 3 were not previously required in any contract.
Under the DFARS 252.204-7012 clause, the NIST SP 800-171 controls only apply to the systems that store, process, or transmit CUI. Under CMMC Level 2, the NIST SP 800-171 controls will also apply to systems than can connect to or provide security for the systems that store, process, or transmit CUI. This change can result in many systems within an organization that were out of scope under DFARS 252.204-7012 being dragged into scope under CMMC, which results in increased costs and frustration as unrelated systems become subject to compliance obligations. Organizations should review their business processes and network architecture to limit the scope of CMMC and minimize the impact of a transition from DFARS 252.204-7012 to CMMC by physically or logically isolating assets that handle CUI from other unrelated assets.
CMMC Level 3 requirements are expected to be limited to certain highly sensitive types of CUI and significant aggregations of CUI as per a DoD memo on CMMC Assessment Levels. The Level 3 requirements are based on the existing NIST SP 800-172 requirements, but there are no FAR or DFARS clauses prior to CMMC that required their implementation, so almost no organizations have implemented these controls. Organizations that expect to be subject to CMMC Level 3 requirements will need to be prepared to add these new controls to their existing NIST SP 800-171 program. DoD estimates only about 1% of defense contractors will be subject to CMMC Level 3 requirements.
Organizations in the DoD supply chain that handle FCI and/or CUI need to be ready for the CMMC rollout. See our other post, A Big Step on the CMMC Rollout Timeline, for more information on the rollout schedule. TrustedSec is available to help organizations prepare for CMMC, whether they have existing FAR 52.204-21, DFARS 252.204-7012, and NIST SP 800-171 programs or they are starting from scratch to meet potential future CMMC obligations, by helping understand scope, assessing their current compliance status, making recommendations for addressing compliance gaps, and assisting with the remediation of compliance gaps. TrustedSec specializes in helping organizations understand the scope of their compliance obligations and working to reduce the cost and effort required to achieve CMMC compliance by analyzing and recommending adjustments to business processes and network architecture that will minimize the scope and impact of CMMC within the environment. Get in touch with us if you need assistance!