CMMC Subcontractors and Service Providers

Table of contents
Defense contractors are preparing their systems for the start of the upcoming CMMC rollout but what they may not have considered is how their relationship with Subcontractors and External Service Providers (ESPs), including Cloud Service Providers (CSPs), may result in their non-compliance with CMMC.
Similarly, a wide variety of IT and Information Security procurement, support, managed service, staff augmentation, and cloud service providers may not realize that CMMC is applicable to their services based on the information they handle on behalf of their customers and that they may lose customers if they cannot demonstrate CMMC compliance.
This post will help contractors, referred to as Organizations Seeking Assessment (OSAs) in CMMC, understand how CMMC applies to their Subcontractors and External Service Providers. It will also help service providers understand how CMMC may apply to them and what their customers’ expectations will be.
TrustedSec is a CMMC Registered Practitioner Organization (RPO) that can help contractors, Subcontractors, and service providers understand if they have obligations under CMMC and implement appropriate solutions to demonstrate compliance. Please get in touch with us if you need any help understanding your compliance program and engaging with customers or service providers.
Concerns
This post was inspired by five concerns based on misconceptions that I’ve repeatedly come across when helping contractors and service providers become CMMC compliant:
- Contractors may not understand the difference between a Subcontractor and an External Service Provider.
- Contractors and External Service Providers may not realize how many different types of IT and Information Security services will be in scope for CMMC as a result of the handling of SPD.
- Contractors and External Service Providers may not realize that each individual contractor must include their External Service Providers within the scope of the contractor’s CMMC assessment if the External Service Provider has not voluntarily undergone a CMMC certification assessment.
- Contractors and Cloud Service Providers may not realize that Cloud Service Providers that handle SPD, but not CUI, are required to implement the CMMC requirements, not the FedRAMP requirements and that these requirements differ from each other.
- Contractors and Cloud Service Providers may not realize the amount of sensitive security information that the Cloud Service Provider will be required to deliver to their customer to demonstrate FedRAMP compliance if the Cloud Service Provider does not have a FedRAMP Authorization.
Each of these presents a challenge that contractors and External Service Providers should understand and address well in advance of an audit to avoid disrupting contractor and service provider relationships.
Overview
Contractors with CMMC obligations at any CMMC Level are responsible for passing CMMC requirements on to Subcontractors when applicable and verifying the Subcontractor’s CMMC compliance before executing a subcontract.
CMMC Level 2 and 3 contractors also cannot be CMMC compliant until they verify that third-parties that handle CUI and/or SPD while supporting the contractor’s IT and/or cybersecurity operations (referred to in CMMC as External Service Providers) meet either CMMC or FedRAMP requirements as applicable.
Care should be taken to differentiate between Subcontractors and External Service Providers. While there are CMMC compliance obligations for both Subcontractors and External Service Providers, the way these obligations are imposed differ.
Care should also be taken to differentiate between the types of information handled by an External Service Provider (CUI vs. SPD) and the type of service provided (cloud vs. non-cloud) as these both affect the type and extent of the compliance obligation imposed on the External Service Provider.
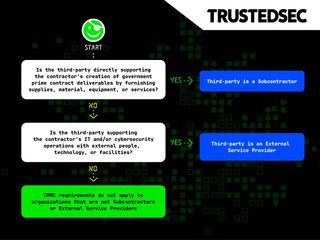
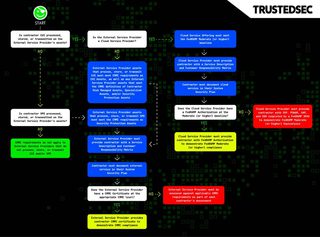
The following flowchart shows CMMC applicability and requirements for all Subcontractors and External Service Providers. The concepts in this flowchart are broken down in more detail throughout this post.

Subcontractors vs External Service Providers
Understanding the difference between a Subcontractor and an External Service Provider within CMMC is necessary to determine whether a third-party is subject to the CMMC subcontracting terms at DFARS 252.204-7021(f) or the CMMC External Service Provider requirements at 32 CFR 170.19(c)(2)(i) for Level 2 and 32 CFR 170.19(d)(2)(i) for Level 3.
Subcontractor is formally defined in 48 CFR 3.502-1 while External Service Provider is defined in 32 CFR 170.4(b). At the risk of oversimplifying these definitions:
- Subcontractors directly support the creation of government prime contract deliverables by furnishing supplies, material, equipment, or services.
- External Service Providers support the contractor’s IT and/or cybersecurity operations with external people, technology, or facilities.
If a third-party is directly contributing the contract deliverable, they should be considered a Subcontractor. Only third-parties that are providing IT and/or cybersecurity services (including cloud services) should be considered External Service Providers. Third-parties that do not fall into either of these definitions are not Subcontractors or External Service providers and CMMC does not apply.
Subcontractor Requirements
When subcontracting, the contractor must insert the full DFARS 252.204-7021 CMMC clause in the subcontract as per DFARS 252.204-7021(f)(1).
Pushing down compliance clauses to Subcontractors should not be a new concept for contractors that will be subject to CMMC. Defense contractors should already be receiving and including the FAR 52.204-21 FCI safeguarding clause and DFARS 252.204-7012 CUI safeguarding clause in their subcontracts as per FAR 52.204-21(c) and DFARS 252.204-7012(m). CMMC supplements but does not replace these clauses, so these obligations will remain in future contracts as well.
What differs in the CMMC clause is that the contractor is required to impose an appropriate CMMC Level and assessment type on the Subcontractor based on the information being flowed down to the Subcontractor as shown in the table below (based on 32 CFR 170.23), even if this differs from the requirements imposed on the contractor.
Highest level information flowed down to Subcontractor | CMMC requirement to be passed on to Subcontractor |
CUI received under a contract with a Level 3 (DIBCAC) requirement | Level 2 (C3PAO) |
CUI received under a contract with a Level 2 (C3PAO) requirement | Level 2 (C3PAO) |
All other CUI, e.g., received under a contract with a Level 2 (Self) requirement | Level 2 (Self) |
FCI | Level 1 (Self) |
While the Subcontractor will be responsible for implementing their own CMMC program, the contractor must still ensure their Subcontractor has a CMMC self-assessment or Certificate at the appropriate Level prior to awarding the subcontract as per DFARS 252.204-7021(f)(2).
External Service Provider Requirements
Applicability to External Service Providers
CMMC applies to an External Service Provider when the External Service Provider’s assets process, store, or transmit CUI and/or SPD on behalf of a defense contractor subject to CMMC Level 2 and/or 3 requirements.
Defense contractors that are only subject to CMMC Level 1 requirements do not need to consider External Service Providers as part of their CMMC compliance scope (according to DoD estimates, this represents approximately 63% of defense contractors). Contractors that are unsure what CMMC Level may apply to them can review our previous post on CMMC Level and Assessment Requirements for Defense Contractors.
Even at CMMC Levels 2 and 3, CMMC External Service Provider requirements only apply if the External Service Provider processes, stores, or transmits CUI and/or SPD. Explanations of CUI and SPD are included in this post for organizations unfamiliar with them.

Examples of External Service Providers that CMMC applies to include:
- Cloud services that contractors use to process, store, or transmit CUI
- Cloud services that contractors use to process, store, or transmit SPD
- Managed SIEM and/or SOC services that ingest logs (SPD) from a CMMC Level 2 or 3 environment
- Vulnerability scanning and penetration testing services that collect vulnerability status information (SPD) about a CMMC Level 2 or 3 environment
- Incident Response and/or forensics teams that access log, configuration, and vulnerability information (all SPD) from a CMMC Level 2 or 3 environment
- Report support, helpdesk, and/or vCISO services that have passwords to access a CMMC Level 2 or 3 environment (SPD)
- Procurement services that handle configuration information (SPD) to configure and install workstations, servers, networking equipment, and/or software in a CMMC Level 2 or 3 environment
- Infrastructure as a service offering that handles configuration information (SPD) for infrastructure underlying a CMMC Level 2 or 3 environment
The DoD Technical Application of CMMC Requirements slides contains additional useful information on the types of service providers that are in scope.
External Service Provider Obligations
External Service Providers are expected to implement the applicable CMMC and/or FedRAMP requirements based on the type of information handled and the type of service provided (as explained below). External Service Providers will also need to demonstrate their compliance with the appropriate CMMC and/or FedRAMP requirements to the contractor by presenting a FedRAMP Authorization or Equivalent, a CMMC Certificate, or being included as part of the contractor’s CMMC assessment.
CMMC requires all External Service Providers to provide their customers with a Service Description and a Customer Responsibility Matrix (CRM). The first step in establishing a relationship between a contractor and an External Service Provider is to share and agree upon these documents.
The Service Description should be a straightforward description of what the service does. The Customer Responsibility Matrix should describe the responsibilities of both the External Service Provider and their customer with respect to the services provided.
A typical format for a Customer Responsibility Matrix is a list of every CMMC control showing which party is responsible for each control and describing how those responsibilities apply. Some requirements may be exclusively handled by the External Service Provider, some may remain the exclusive responsibility of the contractor, and some may be shared responsibilities between both parties. Additional clarifying descriptions are usually necessary for shared controls to clarify the extend of each party’s responsibilities. Keep in mind, at least one party must be responsible for every applicable CMMC requirement. A requirement cannot be considered not applicable simply because neither party wants to take responsibility for it.
The following table is an example of what a few rows of a Customer Responsibility Matrix for a hypothetical service would include:
CMMC Requirement Name | CMMC Requirement | Responsibility | Notes |
RA.L2-3.11.1 Risk Assessments | Periodically assess the risk to organizational operations (including mission, functions, image, or reputation), organizational assets, and individuals, resulting from the operation of organizational systems and the associated processing, storage, or transmission of CUI. | Shared | Service provider annually conducts a risk assessment, using the NIST SP 800-30 methodology, of service provider operations, assets, and individuals resulting from the processing, storage, and transmission of CUI.
Customer is responsible for defining the methodology and frequency with which a risk assessment of customer systems that connect to the service will be performed, and performing that risk assessment as defined. |
RA.L2-3.11.2 Vulnerability Scan | Scan for vulnerabilities in organizational systems and applications periodically and when new vulnerabilities affecting those systems and applications are identified. | Service Provider | Service provider conducts monthly vulnerability scans of all systems and applications that are in scope for CMMC. Additional scans are conducted on in scope systems and applications within 24 hours of an alert indicating a new vulnerability signature is available. Scan results are provided to the customer within 1 business day of scan completion. |
RA.L2-3.11.3 Vulnerability Remediation | Remediate vulnerabilities in accordance with risk assessments. | Customer | Customer is responsible for performing a risk assessment of vulnerabilities identified during scans and from other sources, and for prioritizing and treating vulnerabilities within the system commensurate with risk. |
Contractor Obligations
Contractors are expected to ensure that their External Service Providers comply with the applicable CMMC or FedRAMP requirements as explained below. A contractor is not CMMC compliant until the External Service Providers also meet their compliance obligations.
Contractors are also expected to document their relationship with the External Service Provider and its services in their System Security Plan (SSP). The SSP should contain enough detail to make clear how each CMMC requirement is being met by both the contractor and External Service Provider as supported by the External Service Provider’s Customer Responsibility Matrix. This TrustedSec webinar can help organizations understand how to create an SSP.
It’s important to note that in accordance with the CMMC assessment procedures, a contractor asset that connects to an External Service Provider’s product or service remains in scope for CMMC, e.g., if an external cloud service handles CUI on behalf of a contractor, a contractor workstation connecting to that cloud service is in scope for CMMC. Contractor assets that connect to an External Service Provider must be documented in the SSP and brought into compliance.
Determining External Service Provider Requirements
The specific compliance obligations that a contractor must apply to an External Service Provider under CMMC depend on two things:
- Is the External Service Provider handling CUI or just SPD?
- Is the External Service Provider a Cloud Service Provider?
The answers to these questions result in the following compliance scenarios, each explained in more detail below:
Information and Service Type | Applicable Requirements | Demonstrating Compliance |
Cloud Service Providers handling CUI (possibly handling SPD as well) | FedRAMP Moderate (or higher) baseline | Provide FedRAMPAuthorization or Equivalent to contractor |
Non-Cloud Service Providers handling CUI (possibly handling SPD as well) | CMMC requirements at the appropriate CMMC Level on all CUI Assets, Contractor Risk Managed Assets, Specialized Assets, and Security Protection Assets | Provide CMMC Certificate to contractor or be included in the contractor's CMMC assessment |
Non-Cloud Service Providers handling SPD (but not handling CUI) | CMMC requirements at the appropriate CMMC Level on all Security Protection Assets | Provide CMMC Certificate to contractor or be included in the contractor's CMMC assessment |
Cloud Service Providers handling SPD (but not handling CUI) | CMMC requirements at the appropriate CMMC Level on all Security Protection Assets | Provide CMMC Certificate to contractor or be included in the contractor's CMMC assessment |
Any provider not handling CUI or SPD | None | None |
Cloud vs Non-Cloud Service Providers
Contractors and External Service Providers need to understand what is and is not considered a cloud service in order to apply the correct requirements. Unfortunately, this is mostly a case of “I’ll know it when I see it”, but we have some information that can help understand what DoD considers to be a cloud service.
CMMC defines a Cloud Service Provider at 32 CFR 170.4(b). Some key points from the definition that identify a cloud service include:
- Ubiquitous, convenient, on-demand access
- A shared pool of configurable computing resources
- Rapidly provisioned and released with minimal management effort or service provider interaction
This definition leaves a lot of grey area, but slide 13 of the DoD Technical Application of CMMC Requirements slides provide some more useful indicators of cloud services:
- Services marketed as a cloud offering (_aaS)
- Services acquired as a subscription
The slide also tells us what is not considered a cloud service:
- Hosting the contractor’s leased or owned hardware in a colocation facility or datacenter
- Hosting the contractor’s data on an External Service Provider’s own system similar to shared drives on a local network
- A managed service provider that configures a contractor’s subscribed cloud service
Slide 14 also provides some useful information about managed service providers that administer a cloud environment:
- Managed service providers are not considered Cloud Service Providers when the cloud tenant is subscribed or licensed to the contractor, even if the managed service provider resells the cloud service.
- Managed service providers are considered Cloud Service Providers if they contract with another Cloud Service Provider and further modify the basic cloud service (anything beyond simply configuring and maintaining the service).
- Managed service providers that own a cloud tenant and subdivide it for customer use are likely Cloud Service Providers but could also describe the service as their own system in which case they could be considered a non-cloud service provider.
Requirements for Cloud Service Providers Handling CUI
Cloud Service Providers that handle CUI on behalf of a contractor subject to CMMC must implement the FedRAMP Moderate baseline. This is the same requirement that already exists in the DFARS 252.204-7012 clause at paragraph (b)(2)(ii)(D), so contractors should already be using FedRAMP compliant Cloud Service Providers to handle CUI.
Note that only the FedRAMP Moderate baseline is required and most CUI is not prohibited from leaving the United States. This means that “government” grade cloud services that meet the FedRAMP Moderate baseline and use offshore resources are usually sufficient to meet CMMC cloud service requirements. “Government high” services, which typically meet the FedRAMP High baseline and use domestic locations and personnel, only become necessary when additional specific safeguarding or dissemination controls (e.g., “NOFORN” or “REL TO”) are attached to the CUI.
Keep in mind that some CUI may be covered by other requirements unrelated to the CUI program that may dictate a higher level of protection than is required by the CUI program, e.g., ITAR and/or EAR export controls.
Also note that a FedRAMP Authorization is not required by CMMC or DFARS 252.204-7012. The cloud service only needs to be FedRAMP Equivalent (explained below).
CMMC or NIST SP 800-171 compliance is not a substitute for FedRAMP compliance when a cloud provider is handling CUI. The requirement is clear: FedRAMP Moderate or higher is specifically required for Cloud Service Providers.
FedRAMP Authorization vs Equivalency
Cloud Service Offerings can only gain a FedRAMP Authorization if they are provided directly to a US government agency. This means that Cloud Service Offerings that are available to government contractors, but not the government itself, cannot get a FedRAMP Authorization. The concept of FedRAMP Equivalency was created to allow contractors to use Cloud Service Offerings that are not provided to government agencies.
A FedRAMP Authorization at the appropriate baseline is sufficient to demonstrate that a Cloud Service Offering meets the CMMC requirements handling CUI. No additional information is required besides the Service Description and Customer Responsibility Matrix that is required of all External Service Providers under CMMC.
Cloud Service Offerings that do not have a FedRAMP Authorization will need FedRAMP Equivalency. A DoD memo outlines what is FedRAMP Equivalency means. The Cloud Service Offering must:
- Achieve 100% compliance with the latest FedRAMP Moderate security baseline
- Be assessed as compliant by a FedRAMP recognized Third-party Assessment Organization (3PAO).
A Cloud Service Provider with a FedRAMP Equivalent Cloud Service Offering will need to share the following documentation, referred to as the Body of Evidence (BOE), with their customers to demonstrate compliance:
- FedRAMP System Security Plan (SSP)
- FedRAMP Security Assessment Plan (SAP)
- FedRAMP Security Assessment Report (SAR) performed by a FedRAMP recognized 3PAO
- FedRAMP Plan of Action and Milestones (POA&M)
Many Cloud Service Providers may be hesitant to share this detailed security information with their customers, but it is necessary to demonstrate compliance. Before engaging a Cloud Service Provider, contractors should determine whether the provider has FedRAMP Authorization and Equivalency and confirm that the provider is willing to share the information necessary to demonstrate compliance.
Requirements for Non-Cloud Service Providers Handling CUI
Non-Cloud Service Providers that handle CUI on behalf of a contractor subject to CMMC must implement the CMMC requirements appropriate for the CMMC Level of the CUI they are handling on behalf of the contractor.
How CMMC applies to the External Service Provider will depend on the Customer Responsibility Matrix. Some External Service Providers may want to minimize their own CMMC compliance burden and make the contractor responsible for as many requirements as possible. Other External Service Providers may specialize in making CMMC easy for their customers and may aim to take responsibility for as many requirements as possible. Contractors should consider the effects the Customer Responsibility Matrix will have on their compliance workload when choosing an External Service Provider.
Regardless of the details of each individual Customer Responsibility Matrix, all CMMC requirements must be met wherever they may apply. A CMMC requirement can’t be rendered non-applicable simply because neither the contractor nor the External Service Provider wants to take responsibility for it.
There are two scenarios for a contractor to demonstrate the CMMC compliance of their External Service Providers:
- The service provider has voluntarily undergone a CMMC certification assessment of the appropriate level and type as dictated by the CMMC contract requirement
- The service provider has not undergone a CMMC certification assessment
External Service Providers are not required to undergo a CMMC assessment; however, they are free to do so voluntarily in order to more easily demonstrate compliance to their customers. In this case, the External Service Provider would provide their customers with their CMMC Certificate, which must align with the responsibilities defined in the Customer Responsibility Matrix.
External Service Providers that do not provide a CMMC Certificate are within the scope for their customers’ CMMC assessments. This has negative consequences for both the contractor and the External Service Provider:
- Contractors will need to pay their C3PAO to assess their External Service Providers’ compliance with CMMC unless the contractor is able to self-assess, in which case the contractor must take the time to assess the External Service Provider’s compliance themselves.
- External Service Providers with many defense contractor customers will face a revolving door of C3PAOs and self-assessment customers independently assessing their environment.
- Many External Service Providers will likely be hesitant to share the amount of information required to support an independent assessment with their customers and/or their customers’ C3PAOs.
- Various C3PAOs and customers performing self-assessments may have different interpretations of CMMC requirements, leaving an External Service Provider struggling to “fix” a supposed compliance issue in an environment that was found compliant during a previous assessment.
Assessing an External Service Provider is no small feat. NIST SP 800-171A and NIST SP 800-172A contain the assessment procedures used for CMMC Level 2 and 3 assessments respectively. An assessment includes examining various policies and procedures, interviewing personnel, and testing the environment to ensure that specific assessment objectives for each requirement are in place.
Contractors should strongly consider choosing or moving to External Service Providers that have undergone their own voluntary CMMC certification assessment to avoid the cost and headaches that are sure to come with independent assessments. Similarly, External Service Providers that plan to work with many defense contractors should strongly consider undergoing their own voluntary CMMC certification assessments to avoid the hassle of repeated assessments and make it easier to market their services to customers.
External Service Providers need to be aware of how broad the scope of CMMC is. CMMC applies to assets that process, store, or transmit CUI (CUI Assets) as well as any other assets that are not physically or logically separated from CUI Assets (referred to as Contractor Risk Managed Assets) and assets that provide security functions or capabilities to assets within the CMMC scope (referred to as Security Protection Assets) as detailed in 32 CFR 170.19(c)(1) for CMMC Level 2 and 32 CFR 170.19(d)(1) for CMMC Level 3.
Requirements for Non-Cloud Service Providers Handling SPD (but not CUI)
The requirements for External Service Providers that handle SPD but do not handle CUI are nearly the same as for non-cloud External Service Providers that handle CUI as described above, with only a subtle difference in CMMC scope and applicability: Only the External Service Provider’s systems that handle SPD on behalf of their CMMC customers will need to be brought into compliance with the CMMC requirements relevant to the capabilities provided by the service and will be assessed as Security Protection Assets.
The scope creep issues and requirements related to the handling of CUI, as described above, will not be applicable to the External Service Provider due to the lack of CUI in the environment.
Requirements for Cloud Service Providers Handling SPD (but not CUI)
The requirements for Cloud Service Providers that handle SPD, but not CUI, are the same as the requirements for non-cloud service providers that exclusively handle SPD as described above (demonstrate Security Protection Asset compliance with CMMC either via a voluntary certification or an independent assessment by the customer).
While this may seem simple, there is a catch: most Cloud Service Providers that deal with the US government and its contractors are focused on FedRAMP compliance not CMMC compliance.
I am concerned that many contractors and Cloud Service Providers may not realize that there is a difference between requirements for cloud providers that handle CUI (FedRAMP compliance) and cloud providers that exclusively handle SPD (CMMC compliance). Contractors need to be aware that accepting FedRAMP documentation from Cloud Service Providers that are only handling SPD is likely to lead to unwelcome surprises during C3PAO assessments as the CMMC assessment procedure makes no mention of allowing a FedRAMP Authorization or Equivalent to be used in lieu of compliance with CMMC itself.
Cloud Service Providers that plan to handle SPD on behalf of defense contractors should ensure that they have implemented the CMMC Level 2 and, if necessary, Level 3 requirements. As with other External Service Providers, Cloud Service Providers may find that voluntarily getting a CMMC Certificate is less effort in than submitting to multiple independent customer assessments.
Cloud Service Providers that handle CUI for some contractors and exclusively handle SPD for other contractors will need to ensure they align with the nuances of both FedRAMP and CMMC to meet the needs of all their customers. Although CMMC and FedRAMP are both descended from the NIST SP 800-53 standard, the CMMC requirements do not directly map to FedRAMP.
Subcontractor and External Service Provider Due Diligence
Subcontractors and External Service Providers that have not worked with contracts containing the FAR 52.204-21 (FCI safeguarding), DFARS 252.204-7012 (CUI safeguarding), or DFARS 252.204-7021 (CMMC) contract clauses (including cloud providers that have not implemented FedRAMP and/or CMMC) may not be prepared to demonstrate compliance or may be reluctant to share the required information to demonstrate compliance.
Contractors should consider how they are going to approach CMMC compliance with both Subcontractors and External Service Providers and perform due diligence before executing contracts with any organization that CMMC will apply to. This may include reviewing existing relationships if CMMC requirements will apply to Subcontractors and External Service Providers that DFARS 252.204-7012 requirements have not previously applied to. Some questions include:
- Is the Service Description and Customer Responsibility Matrix suitable for the contractor’s needs?
- Does the Subcontractor or External Service Provider have a CMMC Certificate or FedRAMP Authorization or Equivalent?
- Is the CMMC Certificate or FedRAMP Authorization/Equivalency appropriate for the type of service and information being handled (FedRAMP for Cloud Service Offerings handling CUI, CMMC for all others)?
- Does the scope of the CMMC Certificate or FedRAMP Authorization/Equivalency cover the system or service being offered?
- Is the CMMC Certificate or FedRAMP Authorization/Equivalency current?
- Is the CMMC Certificate or FedRAMP Authorization/Equivalency at an appropriate CMMC Level or Baseline?
- Does the Subcontractor or External Service Provider meet other applicable safeguarding requirements for Categories and/or Limited Dissemination Controls (e.g., data residency) that apply to the CUI?
- Does the Subcontractor or External Service Provider meet other requirements outside the CUI program that apply to the information, e.g., ITAR and/or EAR export control requirements?
- Is the contractor willing to accept the cost and risk of including an External Service Provider without a CMMC Certificate in the contractor’s own CMMC assessment?
- Is the contractor willing to pay the cost of assessing the External Service Provider or will the contractor require the External Service Provider to cover their own assessment cost?
- Is the External Service Provider willing to share the necessary information and access to demonstrate CMMC compliance during the assessment?
- Has the External Service Provider already implemented the required CMMC controls?
- Has the External Service Provider previously passed CMMC assessments conducted on behalf of other customers?
- What is the contractor’s plan if the External Service Provider fails the CMMC assessment?
- Is the contractor willing to wait for a Subcontractor or External Service Provider to become compliant?
- What is the timeline for the Subcontractor or External Service Provider to become compliant?
- What is the contractor’s plan if the Subcontractor or External Service Provider fails to become compliant on time?
Information Definitions
CUI
The scope of CMMC Levels 2 and 3 is based on the presence of CUI so contractors with Level 2 or 3 requirements should already be familiar with how this information flows through their environment, including whether it is handled by External Service Providers.
For service providers not familiar with CUI: This is information that government agencies must safeguard or control the dissemination of due to laws, regulations, or government-wide policies that apply to specifically defined categories of information. Government contractors that receive CUI are contractually obligated to safeguard and control dissemination of CUI on behalf of the government. CMMC is an audit program to ensure contractors are meeting these obligations.
Identifying CUI should be easy: Standardized markings must be applied to all CUI before it leaves the government’s possession, and contractors that create CUI are instructed by the government to apply the standardized markings. Unfortunately, some contractors are confused about what is CUI and when to apply markings, so mismarked documents are floating around the supply chain. See our previous post on Dealing With Unmarked and Mismarked CUI for more information on how to identify legitimate CUI.
SPD
SPD is defined in 32 CFR 170.4(b) as (simplifying a bit) data used to protect a contractor’s environment that is in scope for CMMC. This includes any security relevant information, and the definition explicitly lists the following as SPD:
- Configuration data required to operate in scope security protection assets
- Log files generated or ingested by in scope security protection assets
- Configuration status of in scope assets
- Vulnerability status of in scope assets
- Passwords that grant access to the in-scope environment