Unmasking Business Email Compromise: Safeguarding Organizations in the Digital Age

Business Email Compromises (BEC) within the Microsoft 365 environment are a large threat with nearly $500 Million reported in stolen funds in 2022[1]. Attackers are targeting both company and personal email accounts. It’s important to understand how attackers are accessing mailboxes and learn the best ways to protect yourself.
In case you’re unfamiliar with what exactly a BEC entails, it’s when an attacker or unauthorized user gains access to a business or private email account via social engineering. Most commonly, an attacker compromises an account, intercepts email conversations, and uses the compromised account to send illegitimate communications. The end goal usually involves changing bank account or payment information, requesting gift card purchases, or sending additional email spam.
MFA is No Longer the Silver Bullet
Multi-Factor Authentication (MFA) has long been considered the best method of preventing BEC on email accounts and inboxes. However, as Microsoft began implementing MFA for most tenants, attackers moved to more advanced techniques like Adversary in the Middle (AitM) attacks and MFA Fatigue attacks.
AitM attacks typically start with a social engineering attack, such as phishing, which tricks the user into logging in to their Microsoft 365 account through a malicious site. The malicious site captures credentials and valid session tokens that allows attackers replay the stolen session tokens, allowing them to successfully login and gain access to Microsoft 365 accounts. Once they have access, attackers can set up new MFA devices that allow them to maintain continued access to a mailbox.
Targeted users are also susceptible to MFA Fatigue attacks. These happen when attackers have valid credentials to an account, but do not have access to the MFA token sent to the user. The attacker will keep authenticating and sending requests to the user until they get tired of the requests and click ‘Allow’ just to get them to stop. The attacker then has access to the account.
Attackers will also attempt voice phishing to gain access to mailbox accounts. Attacks will call help desks or on call personal and social engineer their way into having accounts passwords and MFA tokens reset, allowing the attacker to gain access to accounts.
Detection of an AitM attack can vary from attack to attack, but many methods involve the use of Defender for Cloud assets. This allows for detections such as impossible or suspicious travel, suspicious inbox rule activity, suspicious email deletion activity, and activity from an infrequent country.
Inbox Rule Activity
Once an attacker has access to a mailbox, a common action is the creation of inbox rules. These rules usually forward emails to an external email address or marks specific mail as read, followed by forwarding them to a pre-existing folder, most commonly the “RSS Feed” or another folder unlikely to be examined by the user. This allows legitimate conversations to continue to happen but keeps the fraudulent emails hidden from the legitimate user. These fraudulent emails typically involve updating payment accounts to attacker-controlled accounts, updating wire transfer information, requesting gift cards on behalf of executives, or just leveraging accounts to send more spam mail to gain additional access to other internal employees or external contacts.
There are several methods to detect external forwarding or suspicious inbox rules. However, there are two (2) easy actions we rarely see organizations do. The first is to examine all the rules within the organization with a simple PowerShell script to look for any emails being forwarded externally or being moved to suspicious locations.
Connect-ExchangeOnline
$users = (Get-ExoMailbox -resultsize unlimited).UserPrincipalName
foreach ($user in $users)
{
Get-InboxRule -Mailbox $user | Select-Object MailboxOwnerID,Name,Description,Enabled,RedirectTo, MoveToFolder,ForwardTo | Export-CSV RulesOutput.csv -NoTypeInformation -Append
}Second, turn off email forwarding. Forwarding is rarely needed and can be enabled on a case-by-case basis. Microsoft has instructions on how to do so here.
Fast Travel
One (1) of the most common methods to detect BECs are finding successful sign-ins to a Microsoft 365 account from suspicious locations. When attackers log in, they will often do so from locations that are not local to the victim. Typically, these are through third-party VPNs or Tor to maintain the attacker’s anonymity. Examining the location that the user has logged into lets you quickly identify potentially compromised accounts.
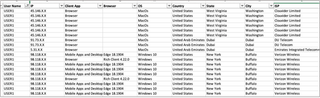
Understand, however, that Microsoft’s geographic locations for IP addresses are not infallible. Additionally, Microsoft’s lookup, only give locations and not services that are associated with the IP address. Therefore, it’s advisable to double-check suspicious IP addresses with intelligence services such as AlienVault OTX, Maxmind, or Spur.
Security Awareness
Users should be educated on how to recognize that their account has been compromised. Common signs can be things such as missing emails or conversations people have sent, receiving multiple MFA prompts when attempting logins, or receiving emails asking if you sent specific emails. If these happen, users should know who to contact to report the issue.
Microsoft Logging
Most commonly, when dealing with these types of attackers, everyone's first questions should be “What emails did the attacker access?” Unfortunately, that is currently a paywalled question. Only the highest tier of Microsoft licensing supports that specific data logging (E5). If a user is on anything else than E5, the email accessed logs are not recorded. In addition, it’s important to validate that audit logging is enabled. While all new tenants have logging enabled via Microsoft by default, older tenants could be running without logging enabled.
Recommendations
There are many different recommendations on how to prevent BEC attacks or limit attack scope, so it is recommended to research which options fit best for the organization. The following recommendations are just a subset of recommendations that are available.
- Phishing Resistant MFA: These can include certificates or FIDO2.
- Enable Security Defaults: This will do some security best practices for a Microsoft 365 tenant including disabling legacy protocols, requiring MFA, and requiring strong passwords.
- More information can be found here: https://learn.microsoft.com/en-us/entra/fundamentals/security-defaults
- Implement Conditional Access Policies: This allows for additional sign-in enforcements when identity-driven signatures are detected such as location, device, etc.
- Security Awareness Training: Continued training to let users know the threats and best practices when it comes to email security and clicking links.
TrustedSec understands that BEC attacks are difficult to detect, time-consuming to investigate, and occur more often than they should. To help organizations, TrustedSec has created a low-cost BEC Investigation offering to help any organization that has suffered an attack. Find out more on our BEC service page.