Webinar Series - Fundamentals of Post-Exploitation with Carlos Perez
Join Carlos Perez (@darkoperator) as he shares some of the post-exploitation methodology used by TrustedSec security consultants performed during actual attack simulations.
Learn the basics of post-exploitation from advanced infosec professionals
Join Carlos Perez (@darkoperator) as he shares some of the post-exploitation methodology used by TrustedSec security consultants performed during actual attack simulations. Each of the four individual webinars will focus on specific aspects that will build upon each other to give a complete picture of the post-exploitation process. New tools will also be released during each individual webinar.
Some of the topics that will be covered, include:
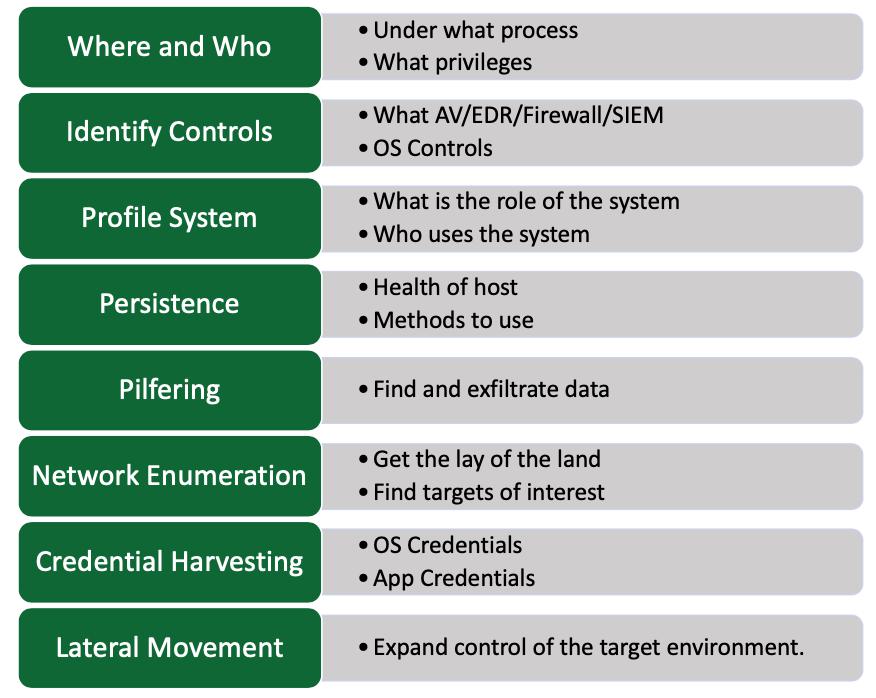
During this series, Carlos will provide an inside look at his process, including…
Webinar 1: Recorded January 16, 2019 at 1:00 PM EST
During the first installment of the series, Carlos will cover what to do after a session is obtained and access has been gained to a host. This section will focus mainly on situational awareness to guarantee that a user’s actions will go unnoticed and how to gather initial information that will guide the toolset and tempo for the operation.
Webinar 2: Recorded January 30, 2019 at 1:00 PM EST
On this webinar, Carlos will provide insight on how to further gather more information on the system. The focus will be placed on the purpose of the system and how it may fit into the network and business process. Lastly, he will show you how to look for the indicators that will determine if this is a system that can stay in memory or if the user should persist.
Webinar 3: Recorded February 27, 2019 at 1:00 PM EST
During the third webinar, Carlos will cover the basics of network enumeration so as to find other hosts in the network and understand the network structure. He will also look at how to find information from users on the system and extract those out of the environment.
Webinar 4: Recorded March 6, 2019 at 1:00 PM EST
On the final of this four-part series, Carlos will provide examples of the different way to collect credentials from the system and how some of the authentication technologies work so as to better abuse them. He’ll also walk-through how to leverage the information we have gathered so far in terms of controls, network environment, and credentials to move laterally across the network. Finally, Carlos will review some of the common techniques and their IOCs in addition to new ones.
