What is a TrustedSec Program Maturity Assessment (PMA)?

Table of contents
The TrustedSec PMA is a tactical approach to evaluating the components, efficiency, and overall maturity of an organization’s Information Security program.
Unlike a traditional compliance audit, the PMA is designed as a strategic business enabler that ensures a security program is strong, adaptive, and resilient. Drawing on best practices from numerous frameworks, plus over a decade of real-world security assessment experience, TrustedSec identifies where your program is strong, where it is vulnerable, and what steps will provide the highest risk reduction and business impact.
Benefits of a PMA
In cybersecurity, standing still is falling behind. Threats evolve daily from ransomware and supply chain compromises to insider risks, and it is essential to continuously evaluate an organization's security posture to ensure it is both technically sound and strategically aligned.
All organizations and their needs are different, which means a one-size-fits-all approach is typically not the best option. TrustedSec solves this by evaluating each organization’s mission, priorities, and current security posture and delivering a set of prioritized recommendations and associated remediation roadmaps that best fit the organization’s needs to minimize risks and safeguard sensitive data.
Benefits include:
- Identify Strengths and Weaknesses: Assessments help pinpoint areas of excellence and those needing improvement, as well as help gain an understanding of the current security posture.
- Mitigate Risks: Identify vulnerabilities before they are exploited by bad actors.
- Enhance Compliance: PMAs can be combined with additional assessments to ensure alignment with industry frameworks and standards or regulations such as NIST CSF, CIS critical Security Controls, and ISO 27001.
- Demonstrate Accountability: Build trust with company stakeholders by showcasing a commitment to robust cybersecurity practices.
- Support Decision-Making: Results from these assessments provide data-driven insights to guide strategic and operational decisions, as well as support the need for purchasing technological tools and/or services.
- Improve Performance: By identifying gaps, organizations can take corrective actions to enhance security program efficiency and business resilience.
- Benchmark Progress: Maturity models often provide benchmarks that allow organizations to compare their progress against industry standards and past assessments.
Key Components and Control Areas
TrustedSec has created the PMA framework based on what we look for in a strong and efficient security program.
The framework starts with the three (3) primary pillars—Enterprise Risk Management, Policy & Standards, and Information Security Architecture. These pillars are supported by additional processes, including Software Development Life Cycle, Identity Access Management, Vulnerability Management, and Threat Management. Each of the pillars and supporting processes contains a set of high-level component areas that dive into the tactical requirements necessary for a mature security program.
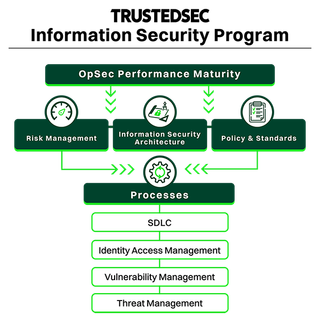
1. Enterprise Risk Management (ERM): The ERM domain addresses the identification, analysis, and mitigation of security risks. Effective ERM includes formalized risk management processes and risk assessments to ensure that the enterprise's risk exposure is in line with risk tolerance goals. The high-level breakdown of the ERM process addresses the following components:
- Organization and Governance
- Definition and Documentation
- Execution and Communication
- Maintenance and Metrics
2. Policy and Standards (P&S): The P&S domain takes a look at the documented policies and standards to ensure they provide clarity on the proper execution of organizational tasks and are approved by leadership. This includes ensuring processes are not only documented but performed as they are written. The high-level breakdown of the P&S process addresses the following components:
- General Best Practices
- Policies
- Standards and Processes
3. Information Security Architecture (ISA): The primary purpose of the ISA domain is to ensure that business strategy and IT security are aligned. The high-level breakdown of the ISA process addresses the following components:
- Alignment and Enforcement
- Architecture Definition
- Configuration Management
- Redundancies
- Segmentation
- Backup Architecture
- Metrics
4. Software Development Life Cycle (SDLC): The SDLC domain is a framework defining tasks performed at each step in the software development process. SDLC is a structure followed by the application development team within the organization and consists of a detailed plan describing how to develop, maintain, and replace specific software, with a focus on security. The high-level breakdown of the SDLC process addresses the following components:
- Organization and Environment
- Planning, Requirements, and Design
- Development and Testing
- Training, Deployment, and Operations
- Maintenance and Metrics
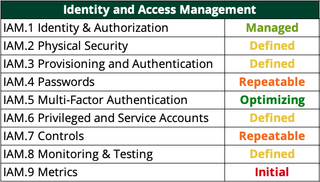
5. Identity Access Management (IAM): The IAM domain deals with the creation, communication, recognition, and usage of identity in the enterprise. The process also ensures that access is appropriately controlled and monitored. The high-level breakdown of the IAM process addresses the following components:
- Identity and Authorization
- Physical Security
- Provisioning and Authentication
- Passwords
- Multi-Factor Authentication
- Privileged and Service Accounts
- Controls
- Monitoring and Testing
- Metrics
6. Vulnerability Management (VM): The VM domain involves the identification, assessing, and addressing of security weaknesses to reduce organizational risks. The organization's VM process is a set of methods, tools, and technologies for discovering, assessing, reporting, and mitigating known vulnerabilities. Patch management is a crucial component of the VM process to ensure vulnerabilities are controlled and not reintroduced. The high-level breakdown of the VM process addresses the following components:
- Organization and Accountability
- Vulnerability Intelligence
- System Hardening
- Vulnerability Discovery
- Patching and Vulnerability Resolution
- Metrics
7. Threat Management (TM): The TM domain deals with the detection and prevention of threats to organizational systems, such as malware, ransomware, malicious actors, and intentional as well as unintentional system misuse by insiders and/or outsiders. The high-level breakdown of the TM domain addresses the following components:
- Organization and Documentation
- Physical Security
- System Controls
- Encryption
- Logging and Monitoring
- Incident Response
- Threat Simulation
- Metrics
What to expect from a PMA?
TrustedSec utilizes a maturity model based on the Capability Maturity Model Index (CMMI) to assess each of the key components that make up a strong security program.

Examples of controls that are covered during a PMA include:
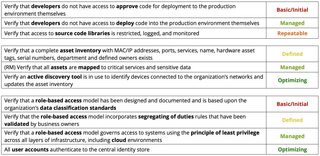
Each of the program areas is quantified to provide the teams with a heat map that can be driven down into detail.
The following is an example of the Executive Summary of a TrustedSec PMA report:
Executive Summary
TrustedSec (see Appendix A: TrustedSec Engagement Team) performed an Information Security Program Assessment to determine the overall state of the Information Security program and provide prioritized recommendations for improvement. The assessment occurred during the period from November 03, 2025 to November 07, 2025. Each recommendation is assigned a Priority Rating based on the risk to the organization.

Based on the assessment findings, TrustedSec has determined that the current Information Security program Maturity Rating at COMPANY XYZ is Repeatable. A detailed explanation of the Maturity Ratings can be found in Appendix B: Maturity Ratings.
A typical PMA takes two (2) to three (3) weeks and follows the below timeline:
- Define Objectives: Determine the goals and scope of the assessment
- Engage Subject Matter Experts (SMEs): Include IT, security teams, HR, leadership, and other applicable stakeholders to ensure a comprehensive evaluation
- Collect Data: Conducted through remote or in-person interviews and by reviewing documentation such as IS policies and network diagrams
- Analyze Results: Map findings against maturity levels and optional industry standards
- Identify Recommendations and Assign Priority Ratings: Develop short, mid, and long-term recommendations to narrow the customer’s focus on specific areas of improvement
- Preliminary Report: Develop and present a preliminary report for the customer’s initial review
- Final Report: Generate a final report after presenting the preliminary report to customer for clarification
Participants in the PMA conversations should be prepared to discuss how mature the organization is for each of the applicable tactical component requirements. This is NOT an audit! The process is intended to identify and prioritize program gaps.
Conclusion
By aligning security processes with organizational priorities, the PMA enables leaders to make informed decisions from a proactive stance by anticipating threats, reducing risk exposure, and strategically investing in the right capabilities at the right time. Rather than reacting to the latest incident or compliance requirement, organizations benefit from knowing that their security strategy is both resilient and adaptable.
Ultimately, this empowers organizations to not only protect their most valuable assets and data but also demonstrate to stakeholders a commitment to security.