Using Azure to Address Endpoint Hygiene Management
Remote workers are set up, but endpoint management is still an issue
Setting up a remote workforce during the COVID-19 pandemic presented a huge challenge, especially trying to get so much done in such a short time frame. While getting extra Zoom licenses was likely pretty easy, there are more challenging issues surrounding remote sharing of documents, endpoint updates, setting up and/or adding more VPN licenses, opening up access to previously restricted vectors, and probably most challenging, answering questions for all of your end users that suddenly blew up the help desk! However, there still may be some core challenges that need to be resolved in ensuring that all machines are updated and in the desired state of configuration.
Automating endpoint hygiene is now a must
Cyber hygiene is typically seen as a set of baseline protections and processes that help to secure an organization. These are the means to attain best practices that, when overlooked, are the most prevalent reason that attackers are able to gain access to systems. However, as most InfoSec people know, understanding what needs to be done is relatively simple, it's the implementation that can be challenging. This is especially true with the increasing complexity of being able to detect, defend, or deter adversaries.
Group Policy is used to address a host of security hygiene areas, including locking down computers, restricting access to specific folders and applications, and changing settings, to name a few. Traditional tactics using Group Policy Objects (GPOs) are still very manual efforts that, with today’s landscape of time and resource constraints, just aren’t going to cut it. Not only are these tactics taxing on your time, they're also increasingly error-prone. Shoring up this area of your security program is going to require converting existing Group Policy processes to cloud-based configuration management to maintain control over endpoints and enable configuration management at scale.
Challenges managing a remote workforce
There are several tasks and support areas that make management efforts more difficult for a larger remote workforce. Maintaining updates, for example, is difficult if a remote worker doesn’t log into the VPN frequently, as is allowing remote workers access to the various files and systems necessary to complete their work. Even assuming there are permissions to modify any GPO, there's the problem of supporting servers and users you can’t physically access. Remote resources can have significantly more configuration drift, as there may be long periods of time where the admin wouldn’t know what settings the resources have and what may have changed. And of course, when it comes to security, it’s also important to know what updates have not been applied. You can’t get reporting back from those Windows 10 machines easily, so you won’t know what has been patched and what hasn't. It can be trying to set a new desired configuration, limit the ability to control changes, and orchestrate changes without impacting uptime. This is especially true when you’re used to starting with Group Policy as the baseline and pushing those requirements onto machines. We have to rethink the essentials.
Taking advantage of the Azure Desired State Configuration
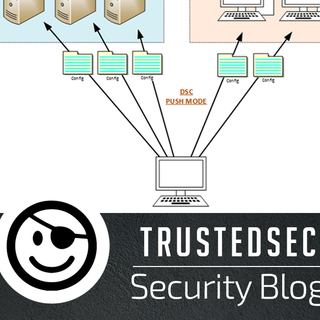
Azure Desired State Configuration (DSC) is a configuration management tool that can assist with the consistency of deploying, monitoring, and updating the desired state of the organization’s IT resources. It can automate and maintain cloud resources using a PowerShell-based workflow engine. The idea is that instead of scripting a configuration, as you would traditionally do with PowerShell, DSC can define how an endpoint should be configured without determining the underlying tasks needed to achieve the desired state. DSC also allows the creation of one configuration with different ways of deploying it, so new systems can work off of that baseline and maintain those configurations without a domain controller. Additionally, DSC can be used to create Incident Response runbooks that can be set up and available if and when issues arise.
Because DSC is cloud-based and managed by Microsoft, some of the burden is eased. Another huge advantage is that it can be pushed out to Linux , Mac, and Windows machines. Any Internet-connected service or platform can be managed with only Internet access and domain membership, meaning that an active VPN connection is not required. Additionally, almost anything you can do with PowerShell can be written into a DSC in simple fashion.
Upcoming Resources:
A DSC can be tough to set up, but once it's ready, it will make your life so much easier. Because this has been a hot topic, in future blogs we’ll cover areas such as:
- Converting Group Policy to DSC
- Advanced Scripting
- Runbooks to Automate Actions
- Secure Credentials
- Version Control
- Integrating With Git
And if you haven’t seen it yet, check out the recent on-demand webinar from TrustedSec!