The Rising Threat: A Surge in Zero-Day Exploits

Introduction
The cat-and-mouse game between defenders and attackers continues to escalate in the ever-evolving cybersecurity landscape. Advanced Persistent Threats (APTs) and cybercriminals are constantly on the lookout for new vulnerabilities to exploit, and one weapon in their arsenal that is gaining traction is the use of zero-day exploits. These elusive and potent attacks are becoming increasingly common as threat actors conduct research, acquire vulnerabilities, and make this information public through proof of concept (POC) code. This blog post will explore how APTs and criminals leverage these zero-day exploits to wreak havoc in the digital world.
Understanding Zero-Day Exploits
Zero-day exploits refer to vulnerabilities in software or hardware that are unknown to the vendor or the security community, leaving zero days for patching or mitigation before they are actively exploited. These vulnerabilities can be found in operating systems, applications, or even firmware, making them a valuable asset for cyber attackers. Once a zero-day becomes public, other groups replicate the exploit; in some cases, a weaponized version is made public, leading to massive exploitation.
These vulnerabilities are identified by a CVE ID. CVE, short for Common Vulnerabilities and Exposures, is a list of publicly disclosed computer security flaws. The CVE program and database is overseen by the MITRE corporation with funding from the Cybersecurity and Infrastructure Security Agency (CISA). Each CVE ID has a Common Vulnerability Scoring System (CVSS), a set of open standards for assigning a number to a vulnerability to assess its severity. This score goes from 1 to 10 where 10 is the highest severity. As practitioners, we prioritize any CVE with a score of 7 or above—7 to 8.9 is considered high and 9 to 10 is critical. We do not discard lower ones since they can be chained with other vulnerabilities to achieve exploitation of a system.
When we look at the distribution of CVSS scores across all CVE IDs issued in the year 2023, we can see that the number of medium, high, and critical are the majority.
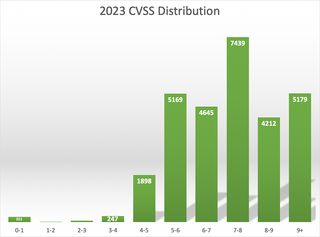
When the high and critical vulnerabilities are broken down by time and we look at each year including the first two (2) weeks of 2024, we can see an increase in almost all categories.
Year | Code Execution | Bypass | Privilege Escalation | Denial of Service | Information Leak |
2022 | 2,067 | 945 | 1,529 | 2,437 | 1,144 |
2023 | 2,579 | 1,048 | 1,514 | 2,557 | 1,547 |
2024 | 130 | 72 | 74 | 206 | 77 |
Research and Discovery
Cybercriminals and APT groups invest significant resources in discovering zero-day vulnerabilities, both monetary and in time. They employ various techniques to identify weaknesses in widely used software, including reverse engineering, fuzzing, and vulnerability scanning. Once they identify a zero-day vulnerability, they keep it secret to maintain its effectiveness; the level of skill to research, find, and weaponize many exploits against modern systems is high. On networking equipment and IoT, the bar is lower. For edge devices, the reward is higher, given the lack of updates and monitoring of these pieces of equipment.
Zero Day Profits
In some cases, threat actors choose to buy zero-day exploits on the dark web or through private underground marketplaces. These transactions can fetch a high price, as the value of a zero-day exploit is often determined by factors such as its severity, the affected software, and the potential impact of an attack. We have also seen the rise of renting exploitation platforms via affiliation schemes in the dark market, where criminal gangs will rent platforms that provide tooling, sometimes including zero days to perform attacks and share a percentage of the profits.
Making Vulnerabilities Public
Surprisingly, some threat actors opt to make zero-day vulnerabilities public by publishing POC code on various forums and websites. This tactic can have far-reaching consequences, as it exposes users to potential attacks before vendors can release patches. The motive behind this behavior can vary, but it often involves spreading chaos or embarrassment to the affected vendors. CISA maintains a list of known vulnerabilities being exploited. We can see that the number is small compared to the CVE IDs issued, but we must also consider that these are the known ones, and many have been exploited for months or longer before a researcher or a vendor saw exploitation and determined the vulnerability. Still, having this information helps us in our risk assessment and prioritizing what vulnerabilities to address first.
Implications of Zero-Day Exploits
The increasing use of zero-day exploits by APTs and cybercriminals poses severe threats to individuals, organizations, and even nations. Here are some of the key implications:
1. Reduced Response Time: Zero-day vulnerabilities leave no room for defenders to prepare, making it crucial to have robust incident response plans and proactive security measures in place.
2. Targeted Attacks: APTs leverage zero-day exploits to carry out highly targeted and sophisticated attacks against specific organizations or individuals, often with political, financial, or espionage motives. As the POCs for the vulnerabilities are made public, we see a shift from targeted exploitation to mass exploitation by every level of threat actor out there.
Mitigating the Threat
To mitigate the threat posed by zero-day exploits, organizations and individuals must take proactive steps:
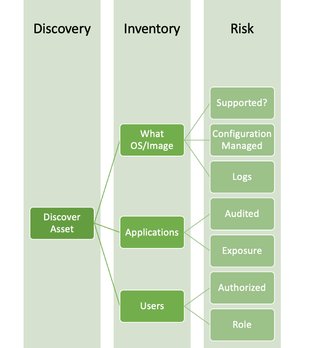
1. Stay Informed: Keep up to date with cybersecurity news and vulnerability disclosures to be aware of potential threats. This is not limited to the results of a Vulnerability Scan but focuses on information related explicitly to one's environment. Knowing the assets, their configuration, and how they fit into the overall systems of the organization will drive how to prioritize what sources of information one will subscribe to in order to be informed of possible zero days surfacing and provide the context to make informed decision in a time-constrained situation. This is why it is important to perform a Risk Assessment to ensure that we are aligning our resources and systems to address these threats properly.
Even when we look at the process at its simplest strategic components, we can see this is not a linear process but one that branches as information is gained and analyzed. It requires the building of systems, relationships across teams, cooperation, and business and technical understanding of where assets fit inside the organizations.
2. Patch Quickly: Implement a robust patch management process to address known vulnerabilities promptly. In addition to quick patching, it is equally important to have the ability to implement mitigations quickly, given that we may not be able to patch a system due to impact to the business, or the patch itself may introduce a risk that needs to be addressed. These are a prerequisite for knowing your environment and having processes to evaluate and test beforehand to minimize risk. I recommend subscribing to the PatchManagement.org mailing list to see how others are addressing patching and learn of any issues with patches to help prevent risks.
3. Employ Defense-in-Depth: Use a layered security approach that includes firewalls, intrusion detection systems, and endpoint protection to reduce the risk of actions taken after zero-day use. Attackers still need to perform myriad actions once they have gained initial access to achieve their target network goals successfully. These actions are known, and we can monitor and alert them once seen. A robust detection system is a priority because environments change as business needs change and new technology stacks get added and modified. One (1) of the main reasons we recommend Purple Team exercises is to provide a base of detections and teach how the process is done. As attacks are made public and information on the Tactics, Techniques and Procedures (TTPs) used by the attackers is made public, one must evaluate if the proper data sources are being ingested in our SIEMs and develop detections to address that behavior. A solution like Impede helps accelerate by providing detections a blue team can build upon quickly.
4. Threat Hunting: In most cases, a zero-day is used by attackers for weeks or even months before it was made public. Having the processes and rehearsed Threat Hunting becomes a critical skill to determine if our network is targeted. In this case, it is important to have external help under retainer to expand the current resources to hunt for actors in a shorter time window depending on the environment's size and complexity.
5. Test: The best way to test the controls and systems that are in place in an environment is to regularly test them, given their nature of constantly changing due to the nature of technology and business. Assumed Breach types of engagements are essential since we are not testing for known initial access techniques but those that come after access is gained. This offers a better value proposition for mature environments. Custom frameworks must be used to allow testers to position themselves on network equipment and IoT devices when possible. Many popular frameworks target large platforms like Windows, macOS, and some Linux but are limited in running on MIPS, ARM, and other platforms in these devices. Examples of these come from Red Team engagements we have done here at TrustedSec whereby laterally moving into SAN solutions, 3D printers, VoIP solutions and even IP cameras, we have been able to avoid detection in nonpermissive environments where our operational tempo and tooling would have been limited on hosts with endpoint security solutions.
Conclusion
The rise of zero-day exploits in the hands of APTs and cybercriminals represents a significant challenge for the cybersecurity community. As threat actors continue to invest in research, purchase exploits, and occasionally make them public, the need for vigilance and proactive security measures has never been greater. Organizations and individuals must remain vigilant, stay informed, and work collectively to defend against these sophisticated and ever-evolving threats.