The Dangers of Transition Mode

Table of contents
With the introduction of WPA3, it is becoming increasingly difficult to successfully exploit a wireless network. One of the main enhancements introduced in WPA3 is the Simultaneous Authentication of Equals (SAE) model. SAE was designed to replace the vulnerable Pre-Shared Key (PSK) method used in WPA2.
A WPA2 Personal network is susceptible to PSK passphrase brute-force attacks, where the 4-way handshake packets are captured during the authentication process. The hashed PSK is then extracted from these packets and transferred off-line in an attempt to recover the cleartext password with an application like Hashcat.
Once the cleartext PSK has been recovered, it can be used to connect to the wireless network and eavesdrop on other connected devices, or potentially used to gain a foothold within the internal network. One of the security enhancements with WPA3 is that the packets remain encrypted, and eavesdropping is not possible, even if the PSK password is guessed or known.
Another security enhancement is that WPA3 networks require the use of Protected Management Frames (PMF). With this requirement, management frames are not vulnerable to PKMID clientless attacks.
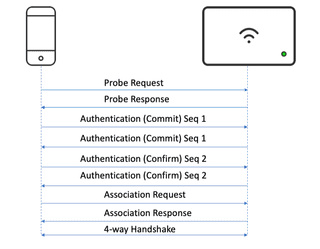
During a recent Wireless Penetration Test, we encountered a wireless network where WPA3 was advertised. Knowing the WPA3 security enhancements, it was assumed this assessment would be quick, with very little to be reported. However, an interesting discovery was made while reviewing the packet capture. The Service Set Identifier (SSID) of the WPA3 network was also being advertised as a WPA2 network.
To recreate the attack, we configured a lab environment with an SSID utilizing WPA3, in order to test what attack possibilities existed. Additional sample sets were collected against a MikroTik wireless router, a Cisco Meraki AP, an Ubiquiti wireless AP, and an Aruba AP.
To begin, we needed to locate and determine visible and hidden SSIDs, hardware information, signal strength, clients connecting, and encryption protocols in use. Within the lab environment, we leveraged the aircrack-ng suite toolkit.
First, we enumerated the SSIDs with airodump-ng. We took note of the channels utilized, as well as the Basic Service Set Identifier (BSSID).
sudo airodump-ng <wlan>
Next, we began capturing packets:
sudo airodump-ng <wlan> --channel <channel> --bssid <bssid> -w captureTip: Click the 'Tab' key when seeing multiple SSIDs to add color for better readability and be able and shift through the list.
Looking at the captured data, we found a wireless network that was configured with WPA3 Personal.

Utilizing Wireshark for analysis, we uploaded the captured packet information and noticed that the captured packet advertised WPA2-PSK and WPA3-SAE. In addition, we observed that PMF protection was enabled for the SSID.
We used the following Wireshark filter to return specific data of our lab SSID:
wlan.fc.type_subtype == 0x0008 && wlan.ssid == <ssid>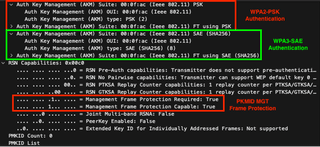
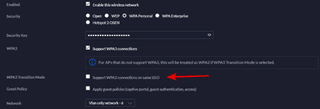
Performing some quick research, it was discovered that the SSID was in transition mode. Transition mode is where WPA3 is interoperable with WPA2 devices and both modes are advertised. Transition mode was created to support the changeover from WPA2 to WPA3. This mode was intended to allow legacy hardware that did not have support for WPA3.

We did find it interesting that each one of the wireless cards only detected WPA3 being advertised for the SSID and not WPA2. Wifite2 was used to perform additional scanning.
Sadly, upon reviewing the Wifite2 repository, there were no references to WPA3 attacks. The kimcoder fork of Wifite2 is still being maintained, so hopefully there will be support for WPA3 attacks in the future.

However, utilizing Wifite2 paid off, and we were successful in capturing a WPA2 handshake. A PKMID attack was also attempted, but this failed due to PMF being enabled.
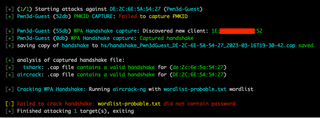
This handshake was taken offline, converted to a useable format, and then brute-forced with Hashcat to recover the plaintext PSK.
Remediation
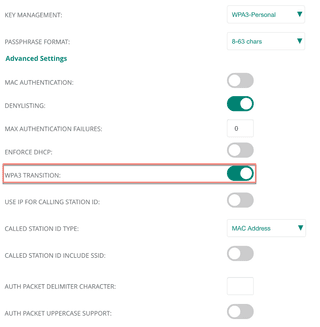
If WPA2 is no longer needed on the network, then disable transition mode. Disabling transition mode is not complicated, pending the AP make and model, simply turn off transition mode or disable WPA2 from the SSID configuration. A reset of the SSID or a reboot of the AP may be required.
If WPA2 is still required due to legacy hardware or applications, configure a strong complexed password and consider periodically changing the password.
Conclusion
As demonstrated, a little creativity goes a long way during a wireless assessment. We wanted to expose the possible false sense of security for those using transition mode within their networks. Continue to utilize a strong PSK password to help mitigate password recovery for captured WPA2 handshakes.
If you have questions or comments, we would love to hear from you! Feel free to reach out on X/Twitter @bond006_5 and @fir3d0g or find us on the TrustedSec Discord.
References
https://www.wi-fi.org/news-events/newsroom/wi-fi-alliance-introduces-wi-fi-certified-wpa3-security
https://www.wi-fi.org/knowledge-center/faq/what-are-protected-management-frames
Recovering WPA2 Handshakes with Hashcat:
https://hashcat.net/wiki/doku.php?id=cracking_wpawpa2
WPA3 Meraki Basics:
MikroTik WiFi Configuration:
https://help.mikrotik.com/docs/display/ROS/WiFi
Aruba WPA3 Configuration:
Cisco WPA3 Deployment Guide:
https://www.cisco.com/c/en/us/td/docs/wireless/controller/9800/technical-reference/wpa3-dg.html
Ubiquiti Unifi: