Technical Analysis: Killer Ultra Malware Targeting EDR Products in Ransomware Attacks

Table of contents
This post was written by John Dwyer, Director of Security Research at Binary Defense, and made possible through the contributions of TrustedSec Senior Research Analyst Kevin Haubris and Eric Gonzalez of Binary Defense.
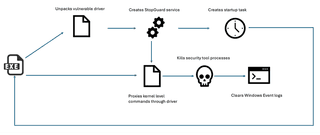
ARC Labs recently recovered a tool leveraged in Qilin ransomware attacks aimed at impairing defenses by disabling popular endpoint detection and response (EDR) and antivirus (AV) tools. ARC Labs has labeled this malware as "Killer Ultra" based on a module name within the malware. Killer Ultra leverages a well-documented Zemana driver as a mechanism to terminate EDR/AV processes; however, ARC Labs have identified additional capabilities within Killer Ultra that indicate it can be leveraged for more than just impairing defenses.
ARC Labs analyzed Killer Ultra to understand its full functionality and provide tactical threat intelligence to organizations to inform their detection and response strategies.
Key Takeaways
- Terminates Processes for Common Security Tools: Killer Ultra obtains Kernel level permissions and targets endpoint security tools from Symantec, Microsoft, and Sentinel One.
- Event Log Clearing: It enumerates and clears all Windows Event Logs.
- Vulnerability Exploitation: Killer Ultra is packed with a vulnerable version of Zemana AntiLogger leveraging CVE-2024-1853 for Arbitrary Process Termination.
- Extended Capabilities: Analysis revealed inactive code with capabilities associated with post-exploitation tools, such as downloading and executing tools over a C2 channel.
CVE-2024-1853
CVE-2024-1853 is an Arbitrary Process Termination vulnerability identified in Zemana AntiLogger v2.74.204.664. This vulnerability exploits the 0x80002048 IOCTL code of the Zemana AntiLogger drivers, allowing an attacker to terminate processes arbitrarily, including critical security processes such as AV or EDR software.
In May 2023, a threat actor with the pseudonym “SpyBoy” incorporated this vulnerability into a tool named “Terminator,” marketed as an "EDR killer" tool. Terminator leverages CVE-2024-1853 by using the vulnerable Zemana AntiLogger driver to disable security solutions on targeted systems. SpyBoy promoted and sold this tool on Russian hacking forums, offering it for prices ranging from $300 for specific AV bypasses to $3000 for an all-in-one solution.
Killer Ultra is packed with the Zemana driver “amsdk.sys,” which is automatically extracted and written to disk in the execution directory of Killer Ultra as a file named “trevor.”
Defense Evasion
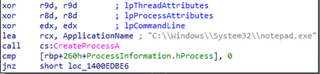
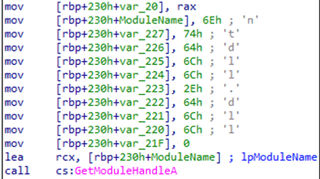
Upon execution, Killer Ultra launches “notepad.exe” via CreateProcessA and opens a handle to “notepad.exe” to overwrite Killer Ultra’s copy of NTDLL with the copy from “notepad.exe.” This appears to be a Userland Unhooking attempt, where Killer Ultra is trying to avoid hooks by endpoint security tools into NTDLL functions by loading a benign copy from “notepad.exe.” Killer Ultra also attempts to further blind endpoint security tools by changing permissions of EtwEventWrite inside of NTDLL, potentially disabling ETW events from being written related to Killer Ultra activities. While ARC Labs verified that the malware executes these functions, it is unclear whether this is actually effective at blinding the malware’s activities from endpoint security tools.
Impair Defenses
After the initialization phase, Killer Ultra loads an unhooked copy of NTDLL from spawning “notepad.exe” and then unpacks the vulnerable Zemana driver to disk. The driver is executed by creating a service named “StopGuard.”
Invoking CreateServiceW creates a registry key in the following location: HKLM\System\ControlSet001\Services\StopGuard with the ImagePath referencing the full path to the extracted “trevor” file.
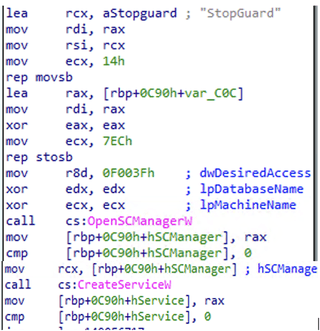
With the driver installed and the service running, Killer Ultra targets a predefined list of security products to disable. The list of security tools is defined by process names which are XOR encoded by 3. Killer Ultra enumerates running processes, and if it finds a process name match, the malware will terminate the process with kernel-level permissions.
Decoding the defined list, Killer Ultra targets the following endpoint security products: Symantec Antivirus, Microsoft Windows Defender, SentinelOne, and Microsoft Defender for Endpoint.
Persistence
To prevent security tools from running again after a system reboot, Killer Ultra creates two scheduled tasks named “Microsoft Security” and “Microsoft Maintenance” to run at system startup. Both tasks are configured to run Killer Ultra at the following path: C:\ProgramData\Microsoft\SystemMaintainence\Maintainence.exe
Indicator Removal
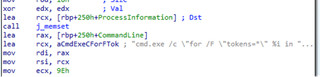
Killer Ultra possesses a subroutine named StartAddress referenced within the main function, designed to remove indicators of compromise by clearing the Windows Event Logs leveraging the “wevtutil.exe” utility. When called, Killer Ultra spawns “wevtutil.exe” via “cmd.exe” to loop through all Windows Event Logs and clear them using the following command:
cmd.exe /c "for /F "tokens=*" %i in ('wevtutil.exe el') DO wevtutil.exe cl %i"
Additional Capabilities
Analysis of the code within Killer Ultra revealed references to capabilities that extend beyond inhibiting defenses. ARC Labs researchers identified inactive functions within the code that could enable Killer Ultra to operate as a post-exploitation tool. While these capabilities are not currently active, these code sections could be activated in future versions of the malware, which is why they will be detailed below to enable organizations to proactively create detections.
Ingress Tool Transfer
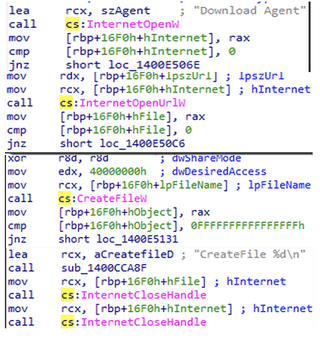
Killer Ultra imports InternetOpenUrlW, CreateFileW, InternetReadFile, and WriteFile functions. Performing cross-reference and code tracing analysis of these function names revealed there are subroutines within the malware capable of downloading tools from remote sources. Specifically, there is a reference to “Download Agent” leveraging InternetOpenUrlW and CreateFileW, indicating that this code could be used in the future to establish a Command-and-Control channel with an impacted system.
Native API Execution
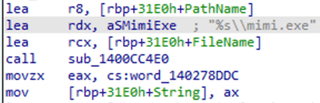
Following the code traces where the downloading functions are referenced, ARC Labs identified Killer Ultra has code designed to execute processes named “mimi.exe” and “program.exe” from “c:\temp” via the native CreateProcessW function.
It is assumed that “mimi.exe” is a reference to the credential harvesting tool Mimikatz, but there is no additional contextual information to determine what “program.exe” is. It is possible that “program.exe” is an arbitrary name that could be a placeholder for any additional tool.
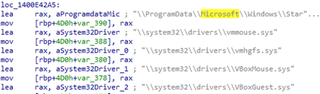
Virtualization / Sandbox Evasion
Killer Ultra contains a list of files associated with virtualization and sandbox software such as VirtualBox and CAPE, which are referenced within a subroutine leading to a call to the ExitProcess function. Analysis of the code could not find an active jump point to this subroutine; however, this functionality could be easily enabled to self-terminate when these files are detected.
Sample Hash:
379e4c80bc7f2d174b5ca9f2decedcee587c73517183488e23e7f34c99371774
Detection Opportunities
ARC Labs has uploaded queries from common endpoint security solutions for Killer Ultra to the ARC Labs Hunting Queries GitHub repository here.