Securing Sensitive Data: How Ransomware Challenges the Healthcare Industry

The healthcare industry is a prime target for ransomware attacks due to the critical nature of its services and the sensitive data it handles. This blog post outlines essential steps that healthcare organizations can take to fortify their defenses against ransomware.
The recent attack against Change Healthcare shows the impact ransomware can have on a business, its partners, customers, and the overall industry. This type of attack is different from others due to the devastating effects on the business, the cost of the system affected, and the ransom (if paid) to free the data. Even with payment, the risk persists with this type of attack.
The key characteristics of a ransomware attack are:
- Encryption and Extortion: Ransomware attacks typically involve encrypting the victim's files or locking users out of the system, making it inaccessible. Attackers demand a ransom payment in exchange for providing the decryption key or unlocking the system and not publicly releasing the stolen information. This direct extortion tactic sets ransomware attacks apart from other types of cyber threats.
- Monetary Motive: Unlike many other cyberattacks that may focus on stealing data or causing disruption, ransomware attacks are primarily financially motivated. Attackers aim to extort money from victims by demanding payment, often in cryptocurrencies like Bitcoin, which provides anonymity and makes tracing the transactions more challenging for authorities.
- Wide-Ranging Impact: Ransomware attacks can have a broad impact, affecting individuals, businesses, organizations, and even critical infrastructure. Because they often target systems or networks crucial for operations, such as healthcare facilities, government agencies, or financial institutions, the consequences can be severe and widespread.
At TrustedSec, we have worked with many customers who have been victims of these attacks, and we have seen firsthand the hardships it causes, from doctors and nurses trying to provide the best care they can with limited tools to the gut-wrenching visuals of ambulances in an ER having to be turned away. One must understand that preparing for this type of attack is a marathon where the best approach to resist, contain, and recover from an attack is a mixture of systems, playbooks, and knowledge.
Mapping Assets and Business Processes to Understand Risk
The first step in securing an IT environment involves finding the assets within that environment, recognizing both the composition of those assets as well as the data contained within and passing through them, and understanding how the assets integrate into various business processes. This step is ongoing, where asset management and constant updating as the system and business evolve is critical. Further, this step allows us to find the business owners, whose involvement in the recovery playbooks is integral, to ensure business processes and recovery (if needed) are handled properly. Without mapping where the critical and sensitive data are located, used, and move, we are not able to protect it.
One part of this step that is often missed is identifying the critical partners that help form our business processes so we can plan what actions would be taken if a partner fell victim to a ransomware attack and find information shared and accessed by that partner. This goes both ways. We need to know what data and level of access third parties have, which will aid in coordination and reporting if necessary.
Backup and Recovery
Formulating a backup and recovery strategy is essential to protect data from loss and enable a speedy recovery in the case of a ransomware attack. In the first step, we have identified where we store information, importance of the information, and how it fits in to the business. With this information we know which systems to back up, how often, and what technologies to use to restore those essential to the operation first. Adopt a 3-2-1 backup policy, which entails maintaining three (3) copies of data in two (2) different media types, with one (1) copy kept physically offsite for disaster recovery (note that cloud storage is not physically offsite, since the attacker may have access from your network to it). Make sure the backup options you select, whether they be physical devices or cloud storage, satisfy your security and compliance needs.
When working on recovery plans and playbooks, it is important that in the event of a ransomware attack, it may be necessary to rebuild the servers that manage the backups and reconfigure the storage in addition to all related networking infrastructure. This may include agreements with vendors to provide support in a timely manner if necessary. If encryption is used, the backup of encrypted material and its key must be considered in terms of what would be the most flexible solution while still following regulations for how to store the information. Recovery of the software, keys, and/or certificates to be able to decrypt data adds a level of complexity that needs to be accounted for.
One critical part of the recovery plan is the ability to search backups for the presence of files and other IOCs to ensure that restored systems do not give an attacker another foothold on the network. This step needs to be documented and rehearsed as part of recovery planning and testing. Searching for IOCs in backups, especially after a ransomware attack given its destructive nature, may be the only way to find what systems were compromised to build a timeline and find patient zero.
Incident Response Planning
Developing and reviewing an incident response strategy and playbooks in advance are essential steps in strengthening an organization's resistance to ransomware attacks. A valuable tool in the development of this plan is performing tabletop exercises to ensure all possibilities are documented and considered in the planning. In addition, having a third party on retainer to aid in the response is important, since this will bring extra resources to help determine the initial point of compromise, confirm data exfiltration, and find IOCs and TTPs to ensure an acceptable risk level is achieved. Organizations may minimize downtime and financial losses by equipping their security teams with the tools they need to respond quickly and efficiently to breaches by proactively creating a thorough response plan. By regularly practicing these playbooks, the team may ensure a well-coordinated and prompt reaction that can lessen the impact of the attack by ingraining the necessary actions and protocols in their response.
Vulnerability and Configuration Management
Vulnerability management plays a pivotal role in mitigating the risk of ransomware attacks by systematically finding, assessing, and addressing weaknesses within an organization's IT infrastructure. We are seeing ransomware groups quickly leverage vulnerabilities in remote software, edge services, and networking appliances. When a proof of concept (POC) is made available, we start seeing mass exploitation withing hours. This is why configuration management plays such a crucial role given that some of the vulnerabilities can be mitigated by changing the configuration of systems while patching is planned, tested, and deployed. Many vulnerabilities also come from misconfiguration and bad defaults that can be addressed with configuration management. Many systems get configured into a vulnerable state by accident as part of day-to-day changes and troubleshooting.
A clear inventory and mapping to business needs ensures that vulnerabilities, which could potentially be exploited by ransomware, are promptly found and remediated before attackers can use them on critical business functions. By continuously scanning for and patching software vulnerabilities, enforcing secure configurations, and keeping systems up to date, organizations can significantly reduce their attack surface. Furthermore, a robust vulnerability management program also involves educating employees about the importance of security practices, thereby strengthening the organization's overall defense mechanism. This not only protects critical data and assets but also maintains business continuity and safeguards the organization's reputation.
Monitoring and Detection
Cyber threat intelligence (CTI) is the gathering, evaluating, and sharing of data about known and unknown cyber-attacks that pose a risk to the environment of an enterprise. Organizations can move from a reactive to a proactive approach to cybersecurity by learning the strategies, methods, and procedures (i.e., TTPs) employed by cybercriminals, especially those that specialize in ransomware.
When access to CTI is possible, build a list of attackers that have targeted:
- Your organization directly
- Your partners
- Your competitors
- Your sector
We recommend you also include results from penetration tests and red team engagements. Once a list is generated, they should be ranked by capability. We then search and collect techniques and include them in the scoring. For this article, we will focus on the healthcare sector for the US and select the top four (4) that amount to over half of the reported attacks.
Here we looked at the top four (4) ransomware groups targeting the healthcare sector in the last six (6) months, mapped their techniques to MITRE inside layers of the ATT&CK Navigator, and aggregated them to see what the top techniques are shared across all groups.

By incorporating CTI into monitoring systems, general surveillance becomes a focused alert for particular hazards. This implies that security teams may prioritize warnings that match the signatures, behaviors, and patterns of known ransomware attacks, rather than having to sort through an influx of notifications. In addition to increasing the effectiveness of monitoring operations, this targeted strategy cuts down on the length of time it takes to identify and address real risks.
With ransomware, the speed and accuracy of detection can mean the difference between a minor disruption and a catastrophic data breach. This is why it is so important that purple team exercises are performed to identify gaps and test detections. Detections need to be adapted and tested for the current environment to reduce the number of false positives and identify via testing any false negatives.
Defensive Efficacy
Another aspect of building defenses to resist ransomware attacks is looking at how effectively an organization’s tools have been deployed. The MITRE ATT&CK® framework is a great resource to determine which tools in the environment can detect which known attack techniques by mapping deployed tools to ATT&CK Data Source and Components.
A simple example is the attack technique Exploitation for Credential Access, a common technique utilized by ransomware initial access brokers to help gain a foothold in a target’s network. The ATT&CK framework shows this technique can be detected by three (3) Data Source:Component pairs:
- Application Log:Application Log Content
- Process:Process Creation
- User Account:User Account Authentication
Following the mapping of deployed tools to ATT&CK Data Sources:Components, it is clear that most endpoint detection and response (EDR) tools have visibility into Process:Process Creation, among others:
On paper, most EDRs should be able to detect the Exploitation for Credential Access technique. However, we don’t yet have a complete understanding of how effectively the tool has been deployed in the environment. It may not be on all endpoints yet, may be deployed in monitor-only mode, or may be a new tool that the Security teams do not have experience with. To better understand how well the tool should be able to detect any technique, it is crucial to look at the tool’s effectiveness. For example:
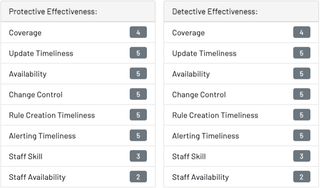
In this example, many of the tool’s effectiveness variables scored in a CMMI-style rating are Very Good (4) or Excellent (5). However, Staff Skill has been given a Good (3) rating, indicating that the team may not have much experience with the tool, and Staff Availability has been given a Fair (2) rating, indicating that the team does not have enough people to effectively analyze indicators of compromise (IOCs) from this tool.
The resulting detective effectiveness heat map for the Exploitation for Credential Access technique might now look more like this, taking into consideration the effectiveness scores of other tools in addition to the EDR:
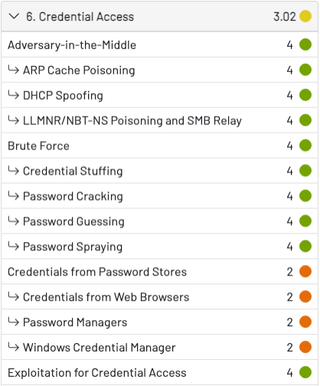
From this perspective, an organization can begin to prioritize how to improve lower tool effectiveness scores that will give the teams a higher likelihood of detecting attack techniques that might currently be missed based on the tool’s effectiveness.
Red Teaming and Penetration Testing to Validate
Performing regular penetration tests and annual red team exercises are important for the overall security posture as controls and detections are gradually put in place. These exercises test the effectiveness of security controls. It's not enough to have defenses in place; organizations must know that they work as intended. Red teaming, in particular, can assess the strength of security measures by bypassing them or exploiting gaps, similar to an adversary. In addition of helping to identify these areas of improvement, red teams can test how well an organization can detect, respond, and recover from an attack. This can significantly improve incident response times and procedures, reducing the potential impact of a real ransomware attack.
These exercises offer a practical training opportunity for security teams. They help teams stay current with the latest attack strategies and defense mechanisms, ensuring readiness against new and evolving ransomware tactics. The insights gained from red teaming and penetration testing should feed back into the organization's security strategy, helping to develop a dynamic and adaptive security posture that evolves in response to the changing cyber threat landscape.
Conclusion
In this blog post, we've stressed the importance of a comprehensive, proactive approach to cybersecurity in the healthcare sector, emphasizing the need for thorough preparation, understanding of one's digital landscape, and having effective response strategies in place to mitigate the severe consequences of ransomware attacks.
The key takeaways are:
- Asset and Business Process Mapping: Identifying and continuously updating the knowledge of assets and how they integrate into business processes is vital. It helps in understanding and preparing for risks effectively. Involvement of business owners is also critical to ensure proper handling of recovery processes.
- Backup and Recovery: Having a robust backup and recovery strategy is essential. This involves regular backups, using various media types, and keeping offsite copies for disaster recovery. This step also necessitates ensuring backups are free of compromises before restoration.
- Incident Response Planning: Organizations must develop and practice incident response strategies and playbooks. Tabletop exercises and third-party retainers for incident response can provide additional support and resources during an attack.
- Vulnerability and Configuration Management: Proactive vulnerability management and proper configuration are key to preventing ransomware from exploiting system weaknesses. This includes addressing vulnerabilities quickly, especially when proofs of concept for exploits are made available.
- Monitoring and Detection: Using CTI to inform monitoring and detection systems is critical for a proactive security posture. Understanding the techniques used by ransomware groups and adapting detection systems accordingly helps in mitigating the threats effectively.