ProxyHelper2: The Sequel

TL;DR Version
Hak5 Pineapples changed their module system in Mark VII's, breaking module compatibility.
ProxyHelper2 is a reimplementation of TrustedSec's original ProxyHelper module by @_Kc57 that works on modern Pineapple hardware.
Here's the new module for Mark VII series Pineapples: https://github.com/hoodoer/proxy-helper-the-sequel/releases
Here's the original module for older Pineapples:
ProxyHelper blog and module repository.
Details:
When doing mobile application assessments, sometimes an application refuses to honor the device proxy settings. The original ProxyHelper module was incredibly useful in situations like this. You could install the module on your Hak5 Pineapple and connect the testing device to the Pineapple WiFi. The original module would let you configure the location of your Burp Suite Proxy and enable forwarding, which would force the application's traffic into Burp Suite Proxy.
Any client sending traffic to ports 80 or 443 would have had their traffic forcibly routed into the Burp Suite Proxy, when properly configured could then intercept that traffic.
Note that ProxyHelper only handles the routing aspect, so you would still need to address Burp Suite Proxy certificates and bypassing any potential certificate pinning that the application may already have in place. A good primer on this can be found in @Tsynack's blog: Android Hacking For Beginners
ProxyHelper2 provides the same functionality as ProxyHelper but for newer Hak5 Pineapple hardware. One addition in the new module allows arbitrary TCP ports to be added to the forwarding beyond just ports 80 and 443, in case your application is using odd ports. The only reason we've rewritten this tool is because Hak5 abandoned their old module development system and implemented a new one in the Mark VII models breaking backwards compatibility.
Setup
The easiest way to install ProxyHelper2 is to use the Hak5 Pineapple online modules feature. Navigate to the Modules & Packages settings, then go to the Modules tab. Click the "Get Available Modules" button, and the modules available in the online repository will be displayed. Select the ProxyHelper2 install button. You can skip the manual installation instructions below.
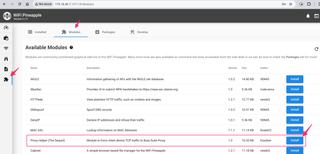
If you prefer to install the module manually you need to download the ProxyHelper2 module file (ProxyHelper2.tar.bz2):
https://github.com/hoodoer/proxy-helper-the-sequel/releases/
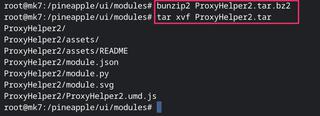
Once you have this file you need to copy it to your Mark VII Pineapple into the /Pineapple/modules directory.

Now you should SSH onto your Pineapple and decompress the module files.
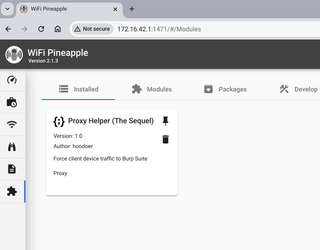
When you refresh your module page in the Pineapple dashboard you'll see the ProxyHelper2 module.
Now would be a good time to configure your Burp Suite Proxy. The proxy needs to be configured to listen on a network device that the Pineapple can reach. By default, Burp Suite Proxy only listens on the localhost loopback device.
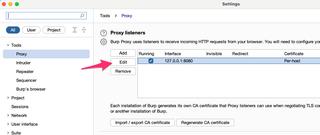
In the proxy settings select the proxy, and choose Edit and change the proxy listener from Loopback only to an appropriate network device. It's easier to simply enable the proxy listener on All interfaces
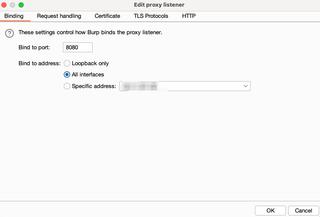
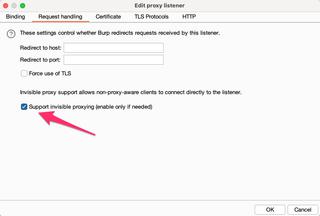
The last configuration change requires setting the proxy to be listening in invisible mode. This is a special mode that assumes traffic coming into the proxy does not include the typical headers that a proxy relies upon. You'll definitely want to disable this configuration when you're done using ProxyHelper2.
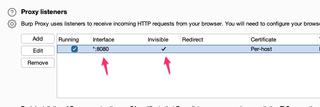
Once this is complete your proxy listing should look similar to below:
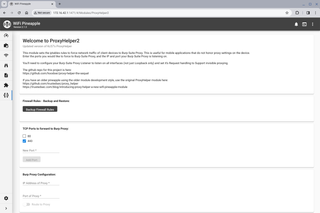
Now we can go back to our Pineapple dashboard and configure ProxyHelper2. In the installed module page click the ProxyHelper2 module to launch the tool.
The best thing you can do is create a backup of your firewall rules. Seriously. Create a backup.
ProxyHelper2 works by setting firewall rules to forcibly route network traffic. You can make as many backups as you wish of the current firewall configuration and restore them later. Backups are stored in /Pineapple/iptablesBackups on the Pineapple device.
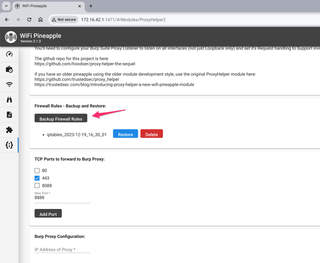
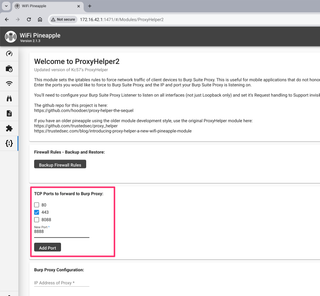
Now, you can select what ports you wish to force to route into Burp Suite Proxy. 443 is selected by default. You can add additional TCP ports as well, and toggle them on and off. You can route multiple TCP ports to Burp Suite Proxy at the same time.
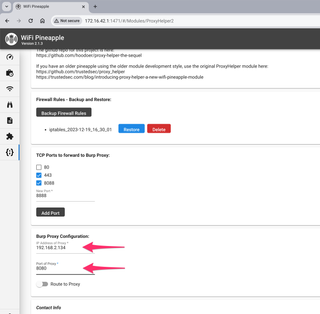
You can now configure the IP address and port that your Burp Suite Proxy is listening on. Remember, your Pineapple must be able to reach the Burp Suite Proxy.
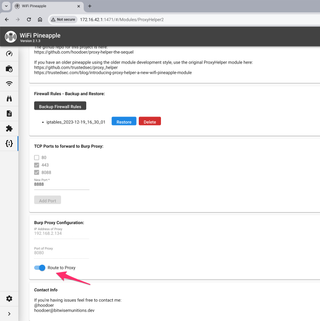
And now you can toggle the proxy routing on. Note that the port forwarding and proxy settings cannot be changed while the routing is enabled.
Here is an example of an Android device's traffic being intercepted by Burp Suite Proxy even though the device does not have a proxy configured.
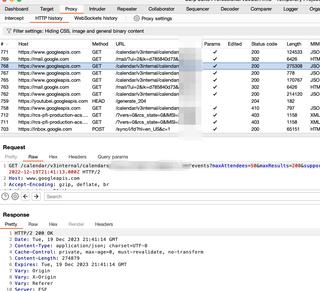
Disabling the routing should return your Pineapple to its normal configuration. If for some reason you're having issues after using ProxyHelper2, restore one of the firewall backups you previously created. You did make one, right?.
That's a quick demo on how to use ProxyHelper2 and a Hak5 Pineapple Mark VII to force device traffic into Burp Suite Proxy.
If you have issues or ideas on how this can be improved, my DMs are always open. @hoodoer.
- https://github.com/hoodoer/proxy-helper-the-sequel (ProxyHelper2)
- https://github.com/trustedsec/proxy_helper (Original ProxyHelper)
- https://trustedsec.com/blog/introducing-proxy-helper-a-new-wifi-Pineapple-module (Original ProxyHelper Blog)