- Blog
- NIST CSF 2.0 Ratings and Assessment Methodologies for Scorecards – When the Math isn’t “Mathing”
NIST CSF 2.0 Ratings and Assessment Methodologies for Scorecards – When the Math isn’t “Mathing”

As a Senior Security Consultant and National Institute of Standards and Technology (NIST) expert, the question I get asked the most is, how do we compare scores and maturity ratings from version 1.1 to version 2.0? Whether it’s being an auditor or auditee, being outside the board room often had the perk of not having to deal with ‘report cards’. On the other hand, understanding the scores when it came to wanting new tools was valuable to justify certain purchases. In consulting, I get the opportunity to see both sides of the problem. With the new changes to 2.0, how does one make sense of the new scorecard, not only from an executive level but as a contributor as well?
Let’s start with some background. Originally, NIST controls or “standards” were geared towards industrial sectors to remove challenges due to competitiveness, dating as far back as 1901. The NIST mission stays constant: “Enable innovation via measurements, standards, and traceability”.
In February of 2024, NIST updated its Cybersecurity Framework (CSF) from version 1.1 to version 2.0. The main intent for updating to NIST CSF 2.0 was to help all organizations be protected against cyber threats and reduce risk. NIST accomplished this by updating CSF guidance to measure up against the original core controls, but also provided traceability for all sectors, not just those specific to industrial. Additional emphasis on governance and supply chain was incorporated. The updated framework is also geared toward all sizes of organizations and sophistication levels, which we will get into with Organizational Profiles.
Defining the variables via setting up the scorecard, what has changed you might be asking? NIST CSF 2.0 now has Governance or Govern (GV) as a separate function for a maturity rating. However, the Govern category itself isn’t totally new. In 2.0, NIST reallocated or moved Governance controls from the previous core control families to create the ‘hub’ for what is now the new functional family Govern. This is to support the new spokes of the updated NIST CSF which still contains the original control families: Identify (ID), Protect (PR), Detect (DE), Respond (RS), and Recover (RC). These families are still intact as far as the standard is concerned and provide traceability as intended, as illustrated below:
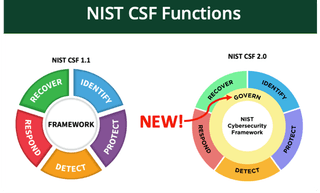
Before we get into ratings, math problems, and scorecards, let’s understand the method to get there. Like math, there are many ways to solve a problem, and there usually is a standard process. As shown below, NIST CSF 2.0 defines the Organizational Profile Process to having a standard way to solve the problem across various organizational types.
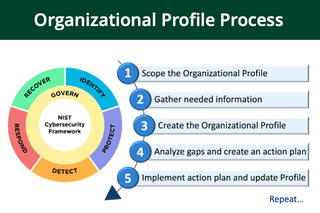
This profile process allows organizations to choose which controls or functions are in scope or out of scope. This can also assist with scoring and maturity if a particular function is no longer in scope or certain controls are not in scope.
More information regarding organizational profiles and gap assessment methodologies can be found via NIST’s guide: https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.1301.pdf
Back to solving math problems; for those going through the 2.0 version for the first time, how do we compare ratings and maturity with the new changes? Is 1.1 equal to 2.0?
When it comes to comparing maturity ratings from old to new, some scores at a functional level (e.g. Identify, Protect, Detect, etc.) may drop slightly due to the reallocation of specific controls, while others may slightly improve, especially if reduced scoping is included.
Sub-functions such as, ID.AM, PR.AA, DE.CM, etc. could drop more than an entire tier for a rating. However, if it’s less than 1 whole point or tier, for those who like averages and 3 significant figures for their scorecards (e.g., 3.75 to 3.25), a half point in one function isn’t a cause for alarm.
The best approach I have found is to carry forward the existing individual controls and assess the 2.0 controls in a new assessment. This can ensure for future assessments a true control-to-control comparison is using only the relevant 2.0 controls.
As far as traceability and measurement, each core or parent function (GV, ID, PR, DE, RS, and RC) and sub-function (e.g., ID.AM, PR.AA,DE.CM,RS.MA, RC.RP) can still be rated to show progression from prior years. NIST also has a mapping spreadsheet from 1.1 to 2.0, but it requires a lot of manual sorting as each control is not a specific 1:1 remapping. Some individual controls will map to various other controls or vice versa.
As someone who deals with mapping various frameworks, I found it easiest to look at each subcategory. For example, governance has subcategories or category identifiers, such as supply chain, risk management, or organizational context. From the old to new versions, these identifiers have remained somewhat consistent compared to the individual controls, as seen below:
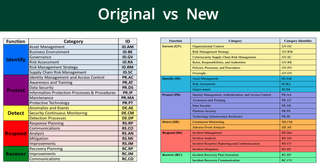
Now for the spreadsheet math. NIST still requires each individual control to be assessed to give a true score of each individual function. As mentioned before, for the scorecard keepers, mapping for traceability across each parent or core function and sub-function is one way to map maturity from 1.1 to 2.0. This method is what I have found to be most effective and is a good way to meet in the middle as companies transition to the new framework.
A common concern is why a score might drop from year to year. Measuring across function and sub-function translates well when having meetings with stakeholders or in the boardroom to show consistency and traceability. Visually seeing the reallocation helps to ease the frustration of the goal post constantly moving, as we typically experience with security standards, regardless of what framework is followed, as seen in my sample spreadsheet images below:
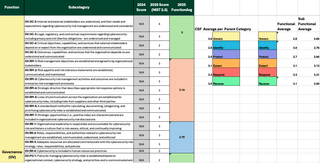
You may be asking, what about the controls that are reallocated or that don’t align with the new sub controls? By sorting through the comparisons, I developed a manual master list to bridge those controls. As seen below, the new controls all have scores for 2.0, while the former controls for each function are now labeled as N/A. By doing this at the sub-function level, the mapping was much easier–not 100% perfect but able to trace for maturity at the sub-function level in a reasonable way.
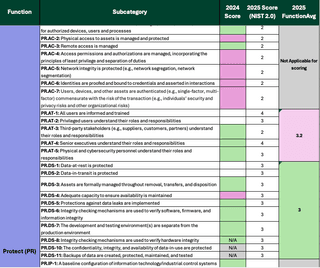
Some groups rate based on subcategory function such as PR-AT as shown above and then take the average of all the sub-category functions (PR.AT, PR.DS, PR.IP, etc.) to get the overall function for Protect. This is also effective if all controls are being assessed individually and can be used for comparing 1.1 to 2.0 at the parent function level.
Another method is to measure Governance separately and still track the other functions at the parent level. This method may not give the traceability we want for Governance until the next assessment, but it still encompasses all functions without adversely affecting scores.
How do we make sure we aren’t missing controls? The simple answer is we refer to the CSF mapping, and when we look at NIST’s documentation of changes from 1.1 to 2.0, we learn that none of the controls were removed, and no new ones were added. The controls were simply reallocated or moved to better fitting categories to align with each parent function.
From a maturity and risk management standpoint, having Governance as the hub helps companies across all sizes and disciplines find a method that works for them for assessing risks and identifying gaps. The key for any assessment is consistency from year to year and understanding that in security, standards are constantly evolving as new threats enter the landscape.
Having a plan after scoping on how to tackle the maturity and gap assessment portion is critical, in addition to being able to map traceability over the years to ensure that the prior year’s findings are being remediated and updated as new changes evolve. This will not only make your program stronger, but it also offers visibility for those on the front lines and in the board room. We don’t need to reinvent the wheel; we just need to be consistent in how we solve the problem.
If you need assistance with NIST CSF assessments or other compliance frameworks, don't hesitate to reach out to TrustedSec for information on our services.