Detection Alchemy - The Purple Team Way

1.1 Introduction
As security practitioners, we frequently extol the virtues of penetration testing and red team exercises as a way of identifying issues for remediation. On the flip side, we also acknowledge the criticality of security tooling such as EDR, firewalls, and SIEMs that can be used to prevent compromise or detect anomalous activity.
However, practically speaking, blue teaming and red teaming tend to operate in silos—and if they aren’t operating separately, they are often in direct opposition to each other.
The reality is that blue and red teaming are different sides of the same coin—each with a distinct but complementary purpose—and should not, in most cases, be treated as separate functions. Thus enters purple teaming.
This post will explore the who/what/where/why (and how) of purple teaming and why it may be worth exploring for your organization.
1.2 What
1.2.1 What is a Purple Team
Most industry professionals are familiar with purple teaming or have at least come across it, even if only as an industry buzzword. However, what purple teaming is can differ across organizations and in third-party implementation. As such, it is important to explain what a purple team is from an industry context, as well as more specifically, how TrustedSec defines and works our purple team engagements.
1.2.1.1 Defining the Teams
Red Team: This is the offensive side. They emulate potential adversaries, conducting simulated attacks against organizational assets.
Blue Team: This is the defensive side. They detect, respond to, and mitigate the compromises executed by the red team.
The Purple Team: While a purple team engagement may differ in offerings, depending on the company being contracted, or even in internal organizational implementations, it almost always refers to the use of offensive and defensive techniques in combination to improve the overall security posture of an organization’s environment.
1.2.2 Early Purple Team Methodology at TrustedSec
Early TrustedSec purple team engagements were often ad-hoc or one-off event-driven engagements, conducted with the purpose of delivering valuable knowledge transfer and high-fidelity detection queries in direct response to specific red team engagements or penetration test findings.
While these exercises are effective and still critical considerations for today’s environments, they often operated in isolation, leading to a lack of communication and missed opportunities to improve the security posture of the organization as a whole. As cyber threats continue to grow in sophistication and number, the need for a more holistic, organized, and systematic approach became clear.
1.2.3 What is a Purple Team Engagement - The TrustedSec Way
Purple Teaming—at least from the TrustedSec perspective—is focused on using real-world tactics, techniques, and tools to execute commands on a remote or local target and then utilize the telemetry generated to build high-fidelity detections within an organization’s SIEM (e.g., Windows Event logs, EDR, JAMF logs, and CloudTrail logs). A significant part of the value of a TrustedSec purple team engagement comes from the combined red and blue perspective that is performed live during the engagement.
It’s important to note that purple teaming is NOT a red team exercise, nor is it an Incident Response or a proactive/reactive Threat Hunting endeavor.
From a red team perspective, TrustedSec consultants will engage the client in providing a knowledge transfer of red team activities:
- Attacker perspective, attribution, motive, and attack execution
- Attacker tooling
- Attacker methodology and attack-path insights
This also includes blue team activities, such as:
- Attack internals (how does it work)
- The underlying telemetry data points and logging requirements
- Data interpretation
- Building the detections using the client’s SIEM query language
- False positive tuning and data interpretation
- Data parsing and regex
Each “detection use-case” is then evaluated from the following perspective: detection, deflection, and deterrence—or what TrustedSec calls the 3D’s.

At the end of an engagement, all findings, detections, and attack commands are provided to the client within the context of a report. This includes a comprehensive pre- and post-(security) posture matrix that evaluates each “attack/detection” finding based upon the defined criteria for detection, deflection, and deterrence.
By leveraging the 3D’s to build a picture of an organization’s pre- and post-engagement security posture, TrustedSec can view the client environment holistically and can build detections that close identified gaps in deterrence and deflection. This perspective allows TrustedSec to help organizations build coverage that will detect the specific TTPs being targeted, but will also alert companies if established first-line defenses fail (e.g. EDR agent failure).
In addition to evaluating an organization’s security posture, TrustedSec will also provide organizations a rating factor that provides an evaluation of how a single specific attack is measured against the 3D’s. This is called a “Defense Resilience Rating.”
Defense Resilience Ratings are estimated based on the combination of identified logs and systems, existing controls, the settings and configurations related to those controls, processes and procedures, monitoring coverage, vulnerability monitoring, patching, and program maturity.
1.2.3.1 Examining a Use-Case Through Kerberoasting
One attack that has shifted from being considered “penetration testing” and “red teaming” focused, and that is now more actively abused by adversaries in the wild, is Kerberoasting. While this post won’t seek to provide background into what Kerberoasting is, or how to attack/detect this technique, it can be featured as a use case to illustrate how TrustedSec would evaluate Kerberoasting attacks conducted within an environment.
So, let’s say this technique is executed.
Given that there is no active “product” on the market that can block this technique (some EDRs exist that can block toolsets like Impacket, which may also block Kerberoasting by proxy—but NOT by technique), TrustedSec would issue a deflection score of “NA.”
With deflection out of the picture for this technique, we can still rely on the other two (2) pillars (i.e., detection and deterrence) to help protect and bolster the readiness of the organization in case this specific attack is executed, allowing a company to build or enhance existing defense-in-depth measures.
For detection, a layering strategy is sought to provide the most comprehensive coverage possible. Such detection strategies may include:
- Tool-specific attribution
- Server-side ticket options and encryption types
- Client-side anomalous source process talking Kerberos (port 88) via non-LSASS
- Correlation between client and server side
- UBA—i.e., Mike in HR requests a service ticket for MSSQLSvc to an SQL server where he has never historically done so before
- A targeted approach by writing to the Service-Principal-Name (SPN) attribute
- Voluminous detection (volume-based or threshold-based detection)
Now, regarding deterrence, the consensus of common controls in the industry (i.e., best practice) is to remove the SPN attribute or to give the SPN account an “uncrackable password” or create “honey SPNs.”
While the attacker may now be able to “perform” the attack, we must question whether the attack is actually “successful” if the attacker is unable to recover a plaintext password. Therefore, if our deterrence controls are well defined, then it no longer matters if the attacker can perform the action of Kerberoasting.
In addition to a “failed” attack (the attacker doesn’t recover a password due to deterrence strategies such as an “uncrackable password”), the attacker will also trigger our detection based on the above listed criteria, as well as a one-two combo punch of a deterrence technique (Honey SPN) plus a detection that alerts upon the Honey SPN being “kerberoasted”. In this case, the attacker has both exposed themselves to defenders and received nothing in return.
1.3 Why
So, we’ve defined purple teaming as a whole, as well as exactly what that means for us here at TrustedSec. But that doesn’t explain the why—or, more specifically, why organizations should pursue purple teaming exercises.
1.3.1 What can a purple team do for my org?
In our experience, SIEM detections are often crafted and implemented with very limited real-world application. This is done either by in-house (blue team) analysts with limited exposure to red team methodology or techniques, or by an MSSP who “installs” the SIEM queries from their pre-generated bank of detections.
In either scenario, they are frequently untested for a specific environment and, depending on the implementor, possibly have little tuning for false positives.
I’m not condemning this way of operating; it’s frequently born out of good intentions. But, let’s be honest here—what good is a detection that doesn’t work?
Worse yet, what happens when you don’t know the detection isn’t working properly? Or, maybe it works, but the analyst looking at it doesn’t understand the function, purpose, or how to respond.
Herein lies the value of a purple teaming, and what we do here at TrustedSec aims to solve both of those issues simultaneously
First, broadly speaking, a TrustedSec purple team exercise has the following four (4) phases:
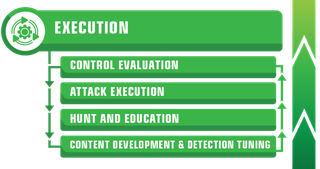
1.3.1.1 Control Evaluation
TrustedSec will begin by assessing the controls around information assets and engaging in a deeper analysis of the identified deflection tools (e.g., AV, NGAV, EDR, IPS, etc.) that can mitigate an attack, as well as the deterrence capabilities (i.e., best practices and deception) implemented by the client. This process is used to highlight possible ingestion sources of logs and other telemetry that will drive the detection methodology.
1.3.1.2 Attack Execution & Detection Crafting (Hunt and Education)
TrustedSec will begin by initiating an attack within your environment. This may be something like a simple password spray or something more specific, such as running BloodHound or other common attack tools that are frequently used by both attackers and penetration testers.
Then, leveraging the telemetry generated from the real attack, TrustedSec will hunt for the activity within your organization’s SIEM, building a custom detection based on the logs generated from a legitimate attack.
1.3.1.3 Validation, Tuning, & Baselining (Content Development & Detection Tuning)
While canned detections absolutely have their place, most experienced analysts will know that tuning to your environment’s baselines is critical, and TrustedSec consultants operate with that knowledge in hand. During your purple team exercise, we are going to tune out the false positives and baseline the activity with you, not for you. This means we leverage the in-house experience of your IT teams to remove known activity up front, as well as TrustedSec’s collective experience to tune out false positives. In addition to general tuning, we will also baseline the activity, ensuring that we catch as many false positives as we can over a period of time, rather than just during a specific point in time.
This attack execution and detection tuning/validation cycle will then be rinsed and repeated several times to ensure holistic coverage of multiple attack avenues, as well as improve tuning and general detection fidelity.
1.3.1.4 Analyst Instruction and Learning
Because our purple team exercises are designed with the express purpose of working with your internal teams, and not in a silo, we have the unique opportunity to provide instruction and explanation for the attacks we execute, as well as the logic for why we are building/tuning/baselining the detection. This real-time and live feedback means that analysts involved in the exercise have more than just a functional detection when we step away—they also have information on the importance and urgency of the attack structure and the understanding of why the detection was built.
1.3.2 Other Benefits
While the main purpose of a TrustedSec purple team is to build actionable and high-fidelity detections, there are a few other things that often go unstated but that we’ve observed as having tangible benefits to the organizations we work with:
- Catching unidentified parsing issues
- Identifying logging configuration issues, either on an ingestion level or a global policy level
- Validating existing detections as well as improvements and reductions in false positive rates
- Adequately assessing security controls on an endpoint/server level
1.4 Where
The TrustedSec purple team exercise is performed live and online in order to maximize client engagement and provide real-time feedback on detection building and attack simulations.
1.5 When & Who
In general, TrustedSec can cater to an organization at any level of maturity, from a newer security program to a more mature one. However, there are a few key indicators that a team is ready for a purple team engagement:
- Has an implemented enterprise SIEM solution
- Is ingesting logs according to operating system/platform best practices
- Has a few penetration testing engagements under their belt and a general idea of current security program limitations
In general, once the above criteria are met, it’s time to schedule your purple teaming engagement.
1.6 Looking Forward - The Future of Purple Teaming
As threat groups continue to evolve, the need for dynamic and adaptive security testing will only increase. Purple team assessments, with their collaborative and proactive approach, will be crucial to this evolution. As technology moves forward with the integration of AI, machine learning, and other technologies that will further shape the attack surface of organizations, purple team methodologies will also need to increase in sophistication in order to stay relevant.
To address these concerns and the continually evolving nature of today’s threat landscapes, TrustedSec has designed new purple teaming methodology. This methodology steps away from detections built as a response to red teaming and penetration testing and engages with real-world TTPs based on annual threat reports, MITRE techniques, and specific client use cases.
1.7 Conclusion
In summation, purple team exercises can provide significant value to an organization that is looking to implement or enhance an existing security policy or detection capabilities and identify gaps in existing security tooling to provide a more holistic view of their environment.