Detecting Password-Spraying in Entra ID Using a Honeypot Account

Table of contents
Password-spraying is a popular technique which involves guessing passwords to gain control of accounts. This automated password-guessing is performed against all users and typically avoids account lockout since the logon attempts with a specific password are performed against every user. This technique is popular with penetration testers, Red Teams, and threat actors alike because it is successful. Password-spray detection typically involves correlating bad password attempts based on time. This detection method is fraught with false positives because standard users mistype and/or forget their passwords regularly. This article describes how to detect Entra ID password-spraying without false positives by leveraging a honeypot account.
For more information on detecting password-spraying in Active Directory, please see my previous blog.
Password-Spraying
Password-spraying tooling works by running through a list of potential passwords and, one by one, attempting to authenticate as each user starting with the first password on this list. If successful, the tool notes this and continues. The tool may pause after completing password-spraying of each password for all users before attempting the next one. This avoids the password lockout policy since the attacker can limit the number of bad password attempts over time.
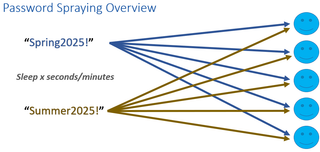
Password-Spraying Approach:
- Attempt authentication for User #1 using Password #1
- Attempt authentication for User #2 using Password #1
- Continue until attempted authentication has been performed using Password #1 for all targeted users
- Pause for a few minutes to avoid account lockout
- Attempt authentication for User #1 using Password #2
- Attempt authentication for User #2 using Password #2
- Continue until attempted authentication has been performed using Password #2 for all targeted users
- Pause for a few minutes to avoid account lockout
Entra ID Password-Spray Detection
One approach is to monitor for failed logons that occur around the same time. This method will likely have false positives. Attackers can also vary their password-sprays so the password attempts occur over a longer period of time to better blend in with standard user activity.
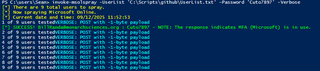
The screenshots below show the MSOLSpray PowerShell tool to password-spray EntraID.
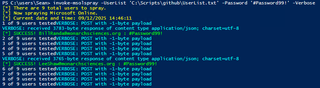
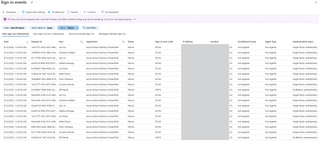
In the screenshot below, we have selected the status field which shows success as well as failed logon attempts. Note that the Sign-in Error Code is 50126 when the password guessed is wrong, and the Sign-in Error Code is 50079 when the password is guessed successfully. In this case, MFA is required so the password was guessed correctly, but MFA was not provided as part of the authentication. When there is a successful authentication using username and password and MFA is not required, the Sign-in Error Code is 0.
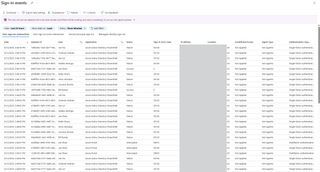
We can change the status to only show failed attempts which can be helpful to identify potential password-spray activity, though the attacker can vary their approach which means attack activity may blend in. Though it is interesting to see that the activity shows the application as “Azure Active Directory PowerShell”. Targeting failed attempts with the application set to Azure Active Directory PowerShell may be related to password-spraying.
We can also see this IP address of the attempted authentication, so we could potentially correlate based on the same IP address or several IP addresses from the same network (or even geo-location).
Entra ID Password-Spray Detection With a Honeypot Account
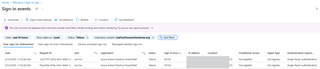
Leveraging a honeypot account is the best way to identify Entra ID password-spray activity because the honeypot account should never have logon activity associated with it. We create a new user (called “Joe Fox” here), which is our honeypot user account. This user does not exist in the organization and therefore should not ever have an associated logon. We can do a test logon with the user so that it looks similar to other regular user accounts.
In this example, I use the account name Joe Fox (UPN: [email protected]). Now, any logon activity associated with the Joe Fox account is related to attacker activity and is likely the result of password-spraying. The benefit here is that we have an IP address, which we can block, and a geographic location.
This information can be used to create an alert in the SIEM that captures the Entra ID sign-in logs.
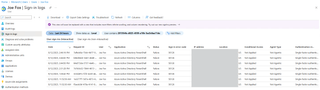
A shortcut to determining the last logon attempt with our honeypot account, Joe Fox, involves opening the user account in the Entra ID portal and clicking Sign-In logs which automatically filters sign-ins for that user as shown in the screenshot below.
Conclusion
Password-spraying Entra ID is a common attack method that can easily be performed by using one of several open-source tools. Detecting this activity typically involves correlating sign-in logs to discover failed logons that occur around the same time. Leveraging a honeypot account provides detection without the false positives.
Please get in touch with us if you need assistance with this topic or would like to learn more about our services.