Basic Authentication Versus CSRF

I was recently involved in an engagement where access was controlled by Basic Authentication. One (1) of the findings I discovered was a Cross-Site Request Forgery (CSRF) vulnerability. The client was unsure of the best approach to prevent CSRF in the context of using Basic Authentication. In this blog post, I will examine the security deficiencies of Basic Authentication, compare it to token-based and JWT-based authentication and authorization, and explore strategies for mitigating CSRF vulnerabilities while utilizing Basic Authentication.
THE DEFICIENCIES OF BASIC AUTHENTICATION
Basic Authentication has been a foundational method of user authentication on the web for decades. However, as technology and security threats evolve, the deficiencies of Basic Authentication have become increasingly apparent. Let’s examine the inherent weaknesses of Basic Authentication and why it’s important to consider alternative authentication methods.
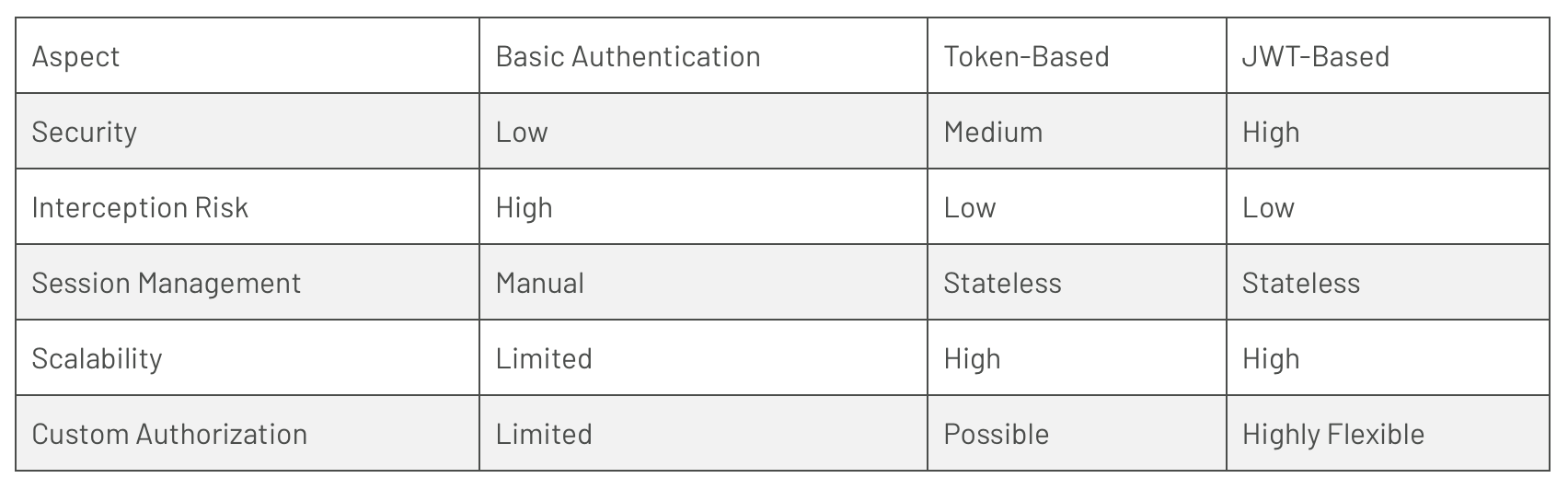
One (1) of the most critical deficiencies of Basic Authentication is the lack of encryption for transmitting credentials. Usernames and passwords are base64-encoded before being sent, making them susceptible to interception by attackers using techniques like packet sniffing. As a result, sensitive information is exposed, jeopardizing user privacy and system security.
Basic Authentication relies solely on the secrecy of the username and password for security. This single-factor authentication is insufficient to defend against various cyber threats, including brute-force attacks, credential stuffing, and dictionary attacks. Once an attacker gains access to valid credentials, they can easily impersonate the user and gain unauthorized entry.
Multi-Factor Authentication (MFA) adds an extra layer of security by requiring users to provide a second form of authentication in addition to their password. Basic Authentication lacks native support for MFA, leaving accounts vulnerable to compromise even if the password is strong. Modern authentication methods, like token-based or JWT-based authentication, offer stronger protection against unauthorized access.
Basic Authentication does not inherently provide session management capabilities. This means that once a user logs in, the session remains active until the browser is closed or a server timeout occurs. In situations where the user forgets to log out, the risk of unauthorized access increases. Modern authentication methods often employ tokens that have a limited lifespan, reducing the window of opportunity for attackers.
Basic Authentication is binary in nature in that it either grants full access or denies it. Fine-grained authorization, such as restricting users to specific sections or actions within an application, is challenging to implement using Basic Authentication alone. More advanced authentication methods, such as JWT-based authentication, allow for the inclusion of custom claims and roles, enabling precise authorization control.
TOKEN-BASED AND JWT-BASED SECURITY
Authentication and authorization play important roles in safeguarding sensitive information and ensuring secure access to resources. Among the various authentication methods, Basic Authentication stands as one (1) of the oldest yet simplest approaches. However, in today’s rapidly evolving threat landscape, it’s essential to understand how Basic Authentication compares to modern counterparts like Token-Based and JWT-Based authentication and authorization.
TOKEN-BASED AUTHENTICATION
Token-Based Authentication is a more robust approach. Here, a token is generated upon successful login and sent with each subsequent request. The server validates the token and grants access if valid. This approach overcomes many of the limitations of Basic Authentication:
- Enhanced Security: Tokens are less susceptible to interception, as they can be transmitted through secure channels (HTTPS). Also, they are typically short-lived, which reduces the window of vulnerability.
- Session Independence: Tokens eliminate the need for keeping session states on the server, resulting in scalability benefits.
JWT-BASED AUTHENTICATION
JSON Web Tokens (JWT) are a specific type of token used for authentication and authorization. They are self-contained, meaning they carry all necessary information within the token itself. This leads to several advantages:
- https://trusted-sec-staging.cl...Reduced Server Load: Since JWTs are self-contained, the server doesn’t need to look up the user’s session or database for validation, resulting in improved performance.
- Statelessness: Like other token-based approaches, JWTs eliminate the need for storing session state on the server, promoting better scalability.
- Enhanced Authorization: JWTs can carry custom claims, allowing for fine-grained authorization based on user roles and permissions.
Basic Authentication vs. Token-Based vs. JWT-Based
PREVENTING CSRF ATTACKS WHEN USING BASIC AUTHENTICATION
CSRF attacks continue to be a serious threat to web applications which can compromise user data and application integrity. While Basic Authentication is a widely used authentication method, it has limitations when it comes to protecting against CSRF attacks. Let’s explore the challenges posed by CSRF attacks in a Basic Authentication environment and discuss effective strategies to prevent them.
CSRF attacks occur when a malicious actor tricks a user into performing an unintended action on a trusted website. These attacks are executed by embedding malicious code or links in a webpage, email, or social media post. When the end-user interacts with the malicious content, the browser sends requests to the trusted website, carrying out actions on behalf of the target user without their knowledge or consent.
CSRF attacks are particularly dangerous when combined with Basic Authentication, as Basic Authentication relies solely on the user’s credentials to authenticate requests, making it challenging to differentiate between legitimate and malicious requests.
Basic Authentication, while a straightforward authentication method, does not inherently provide CSRF protection. It doesn’t include any anti-CSRF tokens or mechanisms by default to prevent unauthorized actions. This absence of built-in CSRF protection makes Basic Authentication applications vulnerable to malicious requests executed by attackers.
EFFECTIVE CSRF PREVENTION STRATEGIES
Preventing CSRF while utilizing Basic Authentication can be challenging. Let’s look at some common approaches you can utilize to prevent this vulnerability:
- Use Anti-CSRF Tokens: Implementing anti-CSRF tokens adds an extra layer of security. Generate a unique token for each authenticated user session and embed it in the HTML forms of your web application. Ensure the token is included in each request and validated on the server side before processing any actions.
- Same-Site Cookies: Configure your cookies to be SameSite, which restricts cookies from being sent in cross-site requests. This helps prevent CSRF attacks by ensuring that only requests originating from the same site can access the authentication credentials.
- Double-Submit Cookie: This technique involves sending two (2) cookies in a request: one (1) in a cookie and the other in a header or request parameter. The server validates that the values match before processing the request.
- Custom Headers: Include custom headers, such as X-Requested-With in requests to help identify legitimate requests. However, note that headers can be modified by attackers in certain scenarios.
- Check Referrer Header: While the Referer header can be spoofed, it can still provide some protection by allowing the server to verify the source of the request.
- Use Content Security Policy (CSP): Implement a strong CSP to mitigate the risks of content injection attacks and reduce the chances of malicious scripts executing in users’ browsers.
- Implement CAPTCHA: Include CAPTCHA challenges in forms to prevent automated requests and bots from submitting malicious actions.
While Basic Authentication is a simple and convenient authentication method, it lacks built-in CSRF protection. As a responsible developer or security professional, it’s important to implement additional measures to prevent CSRF attacks. Combining anti-CSRF tokens, SameSite cookies, custom headers, and other techniques will significantly enhance the security of your web applications, safeguarding user data and maintaining application integrity. Remember that cybersecurity is an ongoing effort, and staying informed about the latest threats and prevention strategies is essential for a robust defense against CSRF attacks.